Table of Contents
This chapter describes security at transport-level and message-level, and how to apply them to JEUS web services.
The following are two ways to apply security to web services.
-
Maintains the security of a connection between client and web service by using SSL.
Transport-level security via SSL secures the connection between a client and JEUS server. However, this secures only the connection itself. If there is an intermediary like a router or a message queue between the client and JEUS server, the intermediary may allow an unencrypted SOAP message to go through. Transport-level security cannot be applied to only a part of the message, but to the whole.
-
Uses digital signature or encryption for SOAP messages.
Message-level security provides the strength of security through SSL as well as additional flexibility. Message-level security is an end-to-end security that maintains the security through multiple intermediaries when transmitting a message. In addition to securing the connection, it provides digital signature and encryption for a SOAP message. The digital signature and encryption can also be applied to only a part of the message.
Transport-level security for a web service uses SSL to secure a connection between a web service and a client application.
The following is the overall process.
-
Configure SSL on JEUS server
There are no additional processes required for web service development. For more information about setting SSL on JEUS server, refer to "JEUS Web Engine Guide".
-
Configure SSL for the Client Application.
-
Download the certificate. (Save the certificate in the local directory via the Internet Explorer.)
-
Store the certificate in the key store.
-
When creating a stub from WSDL using wsimport, or when executing the client to invoke a web service, configure the system property variables as in the following.
–Djavax.net.ssl.trustStore=keystore_name
–Djavax.net.ssl.trustStorePassword=keystore_password
-
To use the wsimport console tool, additionally configure the following environment variable.
set WSIMPORT_OPTS=-Djavax.net.ssl.trustStore=keystore_name -Djavax.net.ssl.trustStorePassword=keystore_password
-
The following are the web service security specifications for a JEUS web service.
-
Web service security policy (WS-Security Policy)
-
Web service security (WS-Security)
-
Web service security conversation (WS-SecureConversation)
-
Web service trust (WS-Trust)
This section describes each specification definition and scenario.
The WS-Security Policy specification defines assertions that describe how a message is secured and transmitted. The assertions are flexible enough to encompass policies for token, encryption, used mechanism, transport security, etc. The web service security policy is a key element for implementing web service message security.
JEUS web service provides a sample scenario of each message level security type for web services. The policy files, to which the web service security policy of each scenario was applied, can be helpful when applying various types of message security for web services.
The web service security specification defines a standard SOAP extension group. It is used to implement a secure web service that preserves data integrity through XML signature and data confidentiality through XML encryption.
The following are web service security scenarios that use the web service security specification.
-
Strengthened symmetric binding verification function through user name authentication
-
Mutual Certificates Security
-
SAML Authentication through SSL
The following is an example of message security using symmetric binding. As already mentioned, in symmetric binding, both client and server use the same certificate for encrypted key and signature. This example uses the server's certificate. Since there is no method for the server to authenticate the client's identity, it also uses a username token.
The following describes a scenario of username authentication and keystore settings.
-
Scenario
Scenario of username authentication:
-
The client encrypts and signs a request message by using the created symmetric key. To do this, it transmits the message with the symmetric key by using a public key of the server along with the username and password.
-
The server decrypts the symmetric key by using the server's private key, and then uses the symmetric key to decode the client's request message and verify the signature. In addition, it authenticates the client by using the username and password.
-
The server uses the same symmetric key to sign and encrypt a response message, and sends the message without the symmetric key.
-
The client uses the symmetric key in its possession to decode the encrypted response message and verifies the signature with the server's public key.
-
-
Keystore setting
The following are the keystore settings.
Type Description Client Keystore that contains the public key of the server. Server Keystore that contains the private key of the server.
The following example shows message security using asymmetric binding and mutual certificates. Unlike symmetric binding, in asymmetric binding, the client and server use different certificates for encrypted key and signature. They sign with their own private keys and transmit certificate information, so that they can authenticate one another when verifying the signatures.
The following describes a scenario of mutual certificates security and keystore settings.
-
Scenario
Scenario of mutual certificates security:
-
The client signs a request message with its private key, and creates a symmetric key to encrypt the message. The client, then, encrypts the symmetric key by using the server's public key, and transmits a request message with the symmetric key to the server along with the client certificate for authentication.
-
The server decodes the symmetric key by using its private key, and decodes the encrypted message. It authenticates the certificate and verifies the signature with the client's public key.
-
The server uses its own private key to sign the response message and creates a symmetric key to encrypt the message. Then, it uses the client's public key to encrypt the symmetric key and sends it in a response message to the client.
-
The client decodes the symmetric key by using its private key, and decodes the encrypted response message. It also verifies the signature by using the server's public key.
-
-
Keystore setting
The following are the keystore settings.
Type Description Client Keystore that contains the public key of the server Server Keystore that contains the private key of the server
This section describes how to include the Security Assertions Mark-up Language (SAML) token in the SOAP message header by creating and transmitting the SAML token as text through a handler.
To use the SAML token for the actual web service, the SAML token framework, which creates the SAML token, is required.
The development and increase in usage of web services increased the need for exchanging security and authentication information between various web applications resulting in a need for exchange standards. SAML(Security Assertions Mark-up Language) is a language that was developed for this purpose.
SAML provides the following functionalities.
-
Provides XML format for user security information and a format for requesting and transmitting such information.
-
Defines how to use such messages in a protocol such as SOAP.
-
Specifies how to exchange the message in general cases such as web SSO.
-
Supports many mechanisms for protecting personal information. For instance, it determines user properties without exporting the user's identity.
-
Provides a way to process ID information in a format provided by the commonly used technologies such as Unix, Microsoft Windows, X.509, LDAP, DCE and XCML.
-
Provides a function for communicating with the SAML option supported by the system that formulates the metadata schema.
The following is a scenario of SAML authorization over SSL.
-
Scenario
-
The client includes the SAML token in the SOAP message header, and transmits a message through the SSL setting.
-
The server interprets the SAML token included in the SOAP message header, and transmits a response message.
-
Note
Message exchanges between the client and server is all done through the SSL setting of the JEUS server.
The Web Services Secure Conversation (WS-SecureConversation) specification defines the creation and sharing of secure context between a service provider and client. The secure context is used to reduce the overheads during message exchanges. The specification defines the standards for better message level security and more efficient exchanges of multiple messages.
JEUS web service follows the WS-SecureConversation and provides the basic mechanism that defines the security method for multi-message exchanges, and helps to establish the context with a more efficient key or a new key element. This can help improve the overall performance and security for message exchanges.
In symmetric binding, an encrypted key needs to be created whenever a message is exchanged, which may not be suitable for multi-message exchanges. In the example, SecureContext is established for both sides by asymmetric binding during the handshaking process before exchanging the first message through the Secure Conversation. When exchanging messages multiple times, the established SecureContext is used for signature and encryption like in symmetric binding. The authentication process is performed during the first SecureContext establishment process through asymmetric binding.
The following describes a scenario of web services secure conversation and keystore settings.
-
Scenario
Web Services Secure Conversation Scenario:
-
The client signs its own certificate and SecureContext information by using the certificate, and encrypts them with the server's public key to transmit to the server. (Asymmetric binding)
-
After decoding the client's message with its private key and verifying the client's signature, the server responds with a message after establishing SecureContext. (Asymmetric binding)
-
When exchanging messages, the client and server use the SecureContext information to encrypt and sign the message. (Symmetric binding)
-
-
Keystore Setting
The following are the keystore settings.
Type Description Client Keystore that contains the public key of the server Server Keystore that contains the private key of the server
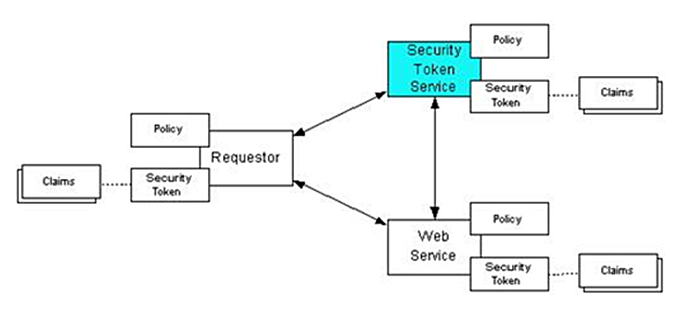
This section describes an example of using WS-Trust for authentication. The certificate between different tokens, which is an untrusted relationship, is converted into the SAML token through STS, and the service provider who cannot trust the service consumer can authenticate it through STS.
To exchange messages using web service security, the service and client should have already agreed upon a security token that is used for sharing security information. Otherwise, a trust relationship must be established between the parties before exchanging messages. This is called a Web Service Trust and is supported by JEUS web services.
Web Service Trust can be used when a server and a client cannot authenticate each other when they each use a different security token or each security token is from a different domain. If they cannot authenticate each other due to different security tokens, another web service, called Security Token Service (STS), can mediate in deciding their authentication roles.
In a trust relationship,
-
A client and the server have no direct trust relationship with each other.
-
A client and an STS have a trust relationship with each other.
-
An STS and the server have a trust relationship with each other.
As shown in the following figure, STS dynamically issues the security token to the requester, so that the web service can authenticate the requester before communicating. The requester transmits a message with the issued security token to the web service, so that it can authenticate(trust) the requester.
*Source: http://docs.oasis-open.org/ws-sx/ws-trust/200512/ws-trust-1.3-os.html
The following is a scenario of web service trust and keystore settings.
-
Scenario
Scenario of Web Service Trust:
-
The client requests STS to issue an SAML certificate for the server, to where the client will transmit the actual message with the client's certificate, and a username and password.
-
STS issues the SAML certificate after authenticating the client.
-
The client transmits a message with the SAML certificate to the server.
-
The server trusts the client through the certificate, and processes the requested business logic.
-
-
Keystore Setting
The following are the keystore settings.
Type Description Client 1. Keystore that contains the client's private key and the server's public key
2. Keystore that contains the client's private key and the STS server's public key
Server Keystore that contains the server's private key and the client's public key STS server Keystore that contains the server's private key and the client's public key
This section introduces common settings applied to the example scenarios of message level security for JEUS web services, and describes how to configure them in each scenario. Refer to the examples to see how they actually work.
Note
The same business logic for the client and web service is used in the message level security configuration example for each scenario.
Common settings applied to example scenarios of message level security in JEUS web service are divided into server and client settings.
The following are some common security settings applied to the 'endpoint-policy-subject', 'operation-policy-subject' and 'input(output)-message-policy-subject' elements.
-
Configuring 'keystore' and 'truststore' elements
The 'keystore' and 'truststore' elements below the 'security-policy' element must be actively set according to the 'security-binding' settings below the 'security-policy' element.
To set a keystore in the 'keystore-filename' element, set the path of the actual keystore file with an absolute or relative path. When using a relative path, the keystore file should be placed in the 'META-INF' directory under the 'classes' directory, which contains the service implementation classes.
[Example 17.1] << jeus-webservices-config.xsd >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <xs:schema xmlns="http://www.tmaxsoft.com/xml/ns/jeus" targetNamespace="http://www.tmaxsoft.com/xml/ns/jeus" xmlns:xs="http://www.w3.org/2001/XMLSchema" elementFormDefault="qualified" attributeFormDefault="unqualified" version="7.0"> ...... <xs:complexType name="keyTruststoreType"> <xs:choice> <xs:element name="keystore-file" type="keyTruststoreFileType" /> <xs:element name="keystore-callbackhandler" type="xs:string" /> </xs:choice> </xs:complexType> <xs:complexType name="keyTruststoreFileType"> <xs:sequence> <xs:element name="alias" type="xs:string" /> <xs:element name="key-type" type="xs:string" minOccurs="0" default="JKS" /> <xs:element name="keystore-password" type="xs:string" /> <xs:element name="keystore-filename" type="xs:string" /> </xs:sequence> </xs:complexType> ...... </xs:schema>
-
Configuring the 'include-token' attribute
The 'include-token' attribute is used to configure whether to include a token in the message.
The following is an example of the X509 token.
[Example 17.2] << jeus-webservices-config.xsd >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <xs:schema xmlns="http://www.tmaxsoft.com/xml/ns/jeus" targetNamespace="http://www.tmaxsoft.com/xml/ns/jeus" xmlns:xs="http://www.w3.org/2001/XMLSchema" elementFormDefault="qualified" attributeFormDefault="unqualified" version="7.0"> ...... <xs:complexType name="x509TokenType"> <xs:sequence> <xs:element name="include-token" type="xs:boolean" minOccurs="0" default="false" /> </xs:sequence> </xs:complexType> ...... </xs:schema>
Note
For more information about other element settings, refer to the 'jeus-webservices-config.xsd' schema, "JEUS Reference Book", and sample examples.
Implementing Web Services from Java Class
To implement web service message security using a Java class, create a web service by using the '-policy' option of the wsgen console tool, as shown in the following example.
$ wsgen fromjava.server.AddNumbersImpl -d web/WEB-INF -policy service-config.xml
Foreknowledge about the contents of 'jeus-webservices-config.xsd', which is JEUS security policy schema for 'service-config.xml' is required to configure the service-config.xml file that is used as an argument of the '-policy' option, .
JEUS security policy schema can set security settings in three elements, 'endpoint-policy-subject', 'operation-policy-subject,' and 'input(output)-message-policy-subject'.
[Example 17.3] << jeus-webservices-config.xsd >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<xs:schema xmlns="http://www.tmaxsoft.com/xml/ns/jeus"
targetNamespace="http://www.tmaxsoft.com/xml/ns/jeus"
xmlns:xs="http://www.w3.org/2001/XMLSchema" elementFormDefault="qualified"
attributeFormDefault="unqualified" version="7.0">
......
<xs:element name="web-services-config" type="web-services-configType" />
<xs:complexType name="web-services-configType">
<xs:choice>
......
<xs:element name="policy" type="policy-configType"
maxOccurs="unbounded" />
</xs:choice>
</xs:complexType>
<xs:complexType name="policy-configType">
<xs:sequence>
<xs:element name="endpoint-policy-subject"
type="endpointPolicySubjectType" maxOccurs="unbounded" />
</xs:sequence>
</xs:complexType>
<xs:complexType name="endpointPolicySubjectType">
<xs:sequence>
......
<xs:element name="security-policy"
type="endpointSecurityPolicyType" minOccurs="0" />
<xs:element name="operation-policy-subject"
type="operationPolicySubjectType" minOccurs="0"
maxOccurs="unbounded" />
</xs:sequence>
</xs:complexType>
<xs:complexType name="operationPolicySubjectType">
<xs:sequence>
<xs:element name="security-policy"
type="operationSecurityPolicyType" minOccurs="0" />
......
<xs:element name="input-message-policy-subject"
type="messagePolicySubjectType" minOccurs="0" />
<xs:element name="output-message-policy-subject"
type="messagePolicySubjectType" minOccurs="0" />
</xs:sequence>
</xs:complexType>
<xs:complexType name="messagePolicySubjectType">
<xs:sequence>
<xs:element name="security-policy" type="messageSecurityPolicyType"
minOccurs="0" />
</xs:sequence>
</xs:complexType>
......
</xs:schema>
The following shows how to configure these three elements.
-
Configuring the 'endpoint-policy-subject' element
Security settings can be configured for each service implementation class. Various settings related to message security, such as security binding (asymmetry and symmetry), signature or encryption, security token, and WS-Security versions, can be configured.
[Example 17.4] << jeus-webservices-config.xsd >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <xs:schema xmlns="http://www.tmaxsoft.com/xml/ns/jeus" targetNamespace="http://www.tmaxsoft.com/xml/ns/jeus" xmlns:xs="http://www.w3.org/2001/XMLSchema" elementFormDefault="qualified" attributeFormDefault="unqualified" version="7.0"> ...... <xs:complexType name="endpointSecurityPolicyType"> <xs:sequence> <xs:element name="security-binding" type="securityBindingType" minOccurs="0" /> <xs:element name="token" type="supportingTokenType" minOccurs="0" /> <xs:element name="protection" type="protectionType" minOccurs="0" /> ...... </xs:sequence> </xs:complexType> ...... </xs:schema>
There are three kinds of security settings for the 'endpoint-policy-subject' element.
-
security-binding
As shown in the following, the security settings for the security-binding element can be set to either 'transport-binding,' 'symmetric-binding,' or 'asymmetric-binding'.
[Example 17.5] << jeus-webservices-config.xsd >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <xs:schema xmlns="http://www.tmaxsoft.com/xml/ns/jeus" targetNamespace="http://www.tmaxsoft.com/xml/ns/jeus" xmlns:xs="http://www.w3.org/2001/XMLSchema" elementFormDefault="qualified" attributeFormDefault="unqualified" version="7.0"> ...... <xs:complexType name="securityBindingType"> <xs:sequence> <xs:choice> <xs:element name="transport-binding" type="transportBindingType" /> <xs:element name="symmetric-binding" type="symmetricBindingType" /> <xs:element name="asymmetric-binding" type="asymmetricBindingType" /> </xs:choice> </xs:sequence> </xs:complexType> ...... </xs:schema>
-
'transport-binding' element
The security setting for the 'transport-binding' element denotes message protection using a transport protocol other than the WS-Security specification (e.g., HTTPS).
[Example 17.6] << jeus-webservices-config.xsd >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <xs:schema xmlns="http://www.tmaxsoft.com/xml/ns/jeus" targetNamespace="http://www.tmaxsoft.com/xml/ns/jeus" xmlns:xs="http://www.w3.org/2001/XMLSchema" elementFormDefault="qualified" attributeFormDefault="unqualified" version="7.0"> ...... <xs:complexType name="transportBindingType"> <xs:sequence> <xs:element name="transport-token" type="tokenType" /> <xs:element name="algorithm-suite" type="algorithmSuiteType" minOccurs="0" default="Basic128" /> <xs:element name="layout" type="layoutType" minOccurs="0" default="Lax" /> <xs:element name="timestamp" type="xs:boolean" minOccurs="0" default="true" /> </xs:sequence> </xs:complexType> ...... </xs:schema>
-
'symmetric-binding' element
The security settings for the 'symmetric-binding' element is used to protect a message through symmetric binding according to the WS-security specification.
Symmetric binding is when the same token is used to encrypt or decrypt a symmetric key. It is used to encrypt or decrypt a message and is transmitted as encrypted below an additional element, EncryptedKey, of the SOAP message header. This means that the same token is used to sign and verify the signature.
The child element, 'protection-token', indicates that the same token is used to encrypt and sign a message.
[Example 17.7] << jeus-webservices-config.xsd >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <xs:schema xmlns="http://www.tmaxsoft.com/xml/ns/jeus" targetNamespace="http://www.tmaxsoft.com/xml/ns/jeus" xmlns:xs="http://www.w3.org/2001/XMLSchema" elementFormDefault="qualified" attributeFormDefault="unqualified" version="7.0"> ...... <xs:complexType name="symmetricBindingType"> <xs:sequence> <xs:element name="protection-token" type="tokenType" /> <xs:element name="algorithm-suite" type="algorithmSuiteType" minOccurs="0" default="Basic128" /> <xs:element name="layout" type="layoutType" minOccurs="0" default="Lax" /> <xs:element name="timestamp" type="xs:boolean" minOccurs="0" default="true" /> <xs:element name="encrypt-signature" type="xs:boolean" minOccurs="0" default="false" /> <xs:element name="encrypt-before-siging" type="xs:boolean" minOccurs="0" default="false" /> </xs:sequence> </xs:complexType> ...... </xs:schema>
-
'asymmetric-binding' element
The security settings for the 'asymmetric-binding' element is used to protect a message through asymmetric binding by following the WS-security specification.
A symmetric binding is when a different token is used to encrypt and decrypt a symmetric key. A symmetric key is used to encrypt or decrypt a message and is transmitted as encrypted below an additional element, EncryptedKey, of the SOAP message header. This means that a different token is used to sign and verify the signature.
[Example 17.8] << jeus-webservices-config.xsd >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <xs:schema xmlns="http://www.tmaxsoft.com/xml/ns/jeus" targetNamespace="http://www.tmaxsoft.com/xml/ns/jeus" xmlns:xs="http://www.w3.org/2001/XMLSchema" elementFormDefault="qualified" attributeFormDefault="unqualified" version="7.0"> ...... <xs:complexType name="asymmetricBindingType"> <xs:sequence> <xs:element name="initiator-token" type="tokenType" /> <xs:element name="recipient-token" type="tokenType" /> <xs:element name="algorithm-suite" type="algorithmSuiteType" minOccurs="0" default="Basic128" /> <xs:element name="layout" type="layoutType" minOccurs="0" default="Strict" /> <xs:element name="timestamp" type="xs:boolean" minOccurs="0" default="true" /> <xs:element name="encrypt-before-siging" type="xs:boolean" minOccurs="0" default="false" /> </xs:sequence> </xs:complexType> ...... </xs:schema>
The following is a description of the child elements.
Division Description initiator-token A token is used by the client to sign a message and also to decrypt an encrypted message from the server. The token is used by the server to encrypt a message and also to verify the client signature.
recipient-token A token is used by the server to sign a message and also to decrypt an encrypted message from the client. The token is used by the client to encrypt a message and also to verify the server signature.
-
-
One of the child elements can be selected for the security setting of the token element.
[Example 17.9] << jeus-webservices-config.xsd >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <xs:schema xmlns="http://www.tmaxsoft.com/xml/ns/jeus" targetNamespace="http://www.tmaxsoft.com/xml/ns/jeus" xmlns:xs="http://www.w3.org/2001/XMLSchema" elementFormDefault="qualified" attributeFormDefault="unqualified" version="7.0"> ...... <xs:complexType name="supportingTokenType"> <xs:choice> <xs:element name="supporting-token" type="tokenType" /> <xs:element name="signed-supporting-token" type="tokenType" /> <xs:element name="endorsing-supporting-token" type="tokenType" /> <xs:element name="signed-endorsing-supporting-token" type="tokenType" /> </xs:choice> </xs:complexType> ...... </xs:schema>
The following is a description of the child elements.
Division Description supporting-token This token value is included in the message header, and can be used to encrypt or decrypt other parts of the message. signed-supporting-token Same as 'supporting-token'. In addition, this token can be signed. endorsing-supporting-token Used to configure a token which is used to resign a signature. Signs the entire 'Signature' element. signed-endorsing-supporting-token Same as 'endorsing-supporting-token'. In addition, this token is signed through the original signature (mutual signing). -
As shown in the following example, one of the child elements can be chosen for the security setting of the protection element.
[Example 17.10] << jeus-webservices-config.xsd >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <xs:schema xmlns="http://www.tmaxsoft.com/xml/ns/jeus" targetNamespace="http://www.tmaxsoft.com/xml/ns/jeus" xmlns:xs="http://www.w3.org/2001/XMLSchema" elementFormDefault="qualified" attributeFormDefault="unqualified" version="7.0"> ...... <xs:complexType name="protectionType"> <xs:sequence> <xs:element name="signed-part" type="protectionPartType" minOccurs="0" /> <xs:element name="encrypted-part" type="protectionPartType" minOccurs="0" /> <xs:element name="signed-element" type="xs:string" minOccurs="0" /> <xs:element name="encrypted-element" type="xs:string" minOccurs="0"> </xs:sequence> </xs:complexType> ...... </xs:schema>
The following is a description of child elements.
Element Description signed-part Part to sign or verify a signature for. encrypted-part Part to encrypt or decrypt. signed-element Part to sign or verify a signature for. This is useful for signing a part of an element. To use this element, the 'disable-streaming-security' element must be set to 'true'. For more information, refer to the example. encrypted-element Part of an element to encrypt or decrypt. This is useful for encrypting a part of an element. To use this element, the 'disable-streaming-security' element must be set to 'true'. For more information, refer to the example.
-
-
Configuring the 'operation-policy-subject' element
Security settings can be configured for each service implementation class method. Additionally, signature, encryption, and security tokens can be configured.
The 'operation-policy-subject' element, which is used to configure security settings for a service implementation class method, is largely divided into the following two types.
[Example 17.11] << jeus-webservices-config.xsd >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <xs:schema xmlns="http://www.tmaxsoft.com/xml/ns/jeus" targetNamespace="http://www.tmaxsoft.com/xml/ns/jeus" xmlns:xs="http://www.w3.org/2001/XMLSchema" elementFormDefault="qualified" attributeFormDefault="unqualified" version="7.0"> ...... <xs:complexType name="operationSecurityPolicyType"> <xs:sequence> <xs:element name="supporting-token" type="supportingTokenType" minOccurs="0" /> <xs:element name="protection" type="protectionType" minOccurs="0" /> </xs:sequence> </xs:complexType> ...... </xs:schema>
The following is a description of the child elements.
Division Description supporting-token Same as the "token" element inside the 'endpoint-policy-subject' element, but this setting only applies to a method. protection Same as the "protection" element inside the 'endpoint-policy-subject' element, but this setting only applies to a method.
-
Configuring the 'input(output)-message-policy-subject' element
Security setting is configured for each parameter and return value of service implementation class methods. Additionally, signature, encryption, and security tokens can be configured.
The following is the security setting for each parameter and return value of service implementation class methods. There are two kinds of security settings for the 'input(output)-message-policy-subject' element.
[Example 17.12] << jeus-webservices-config.xsd >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <xs:schema xmlns="http://www.tmaxsoft.com/xml/ns/jeus" targetNamespace="http://www.tmaxsoft.com/xml/ns/jeus" xmlns:xs="http://www.w3.org/2001/XMLSchema" elementFormDefault="qualified" attributeFormDefault="unqualified" version="7.0"> ...... <xs:complexType name="messageSecurityPolicyType"> <xs:sequence> <xs:element name="supporting-token" type="supportingTokenType" minOccurs="0" /> <xs:element name="protection" type="protectionType" minOccurs="0" /> </xs:sequence> </xs:complexType> ...... </xs:schema>
The following is a description of the child elements.
Division Description supporting-token Same as the "token" element inside the 'endpoint-policy-subject' element, but this setting only applies to the parameters and return values of the method. protection Same as the "protection" element inside the 'endpoint-policy-subject' element, but this setting only applies to the parameters and return values of the method.
Implementing a Web Service from WSDL
To implement a web service from WSDL, configure the message security policy directly in the WSDL document, and create a web service by using the wsimport tool. A simple web service message security can be implemented through WSDL by understanding the WS-SecurityPolicy specification, which is below the WS-policy specification, and applying it to WSDL.
Note
For more information about the WS-SecurityPolicy, refer to: http://docs.oasis-open.org/ws-sx/ws-securitypolicy/200702/ws-securitypolicy-1.2-spec-os.html.
The following is an example of WSDL, with message security configured, that implements a web service.
To set a keystore in the 'keystore-filename' element, set the path of the actual keystore file with an absolute or relative path. When using a relative path, the keystore file should be placed in the 'META-INF' directory under the 'classes' directory, which contains the service implementation classes.
[Example 17.13] << jeus-webservices-config.xsd >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<definitions
...
targetNamespace="http://tmax.com/" name="NewWebServiceService">
<ns1:Policy xmlns:ns1="http://schemas.xmlsoap.org/ws/2004/09/policy"
wsu:Id="NewWebServicePortBindingPolicy">
<ns1:ExactlyOne>
<ns1:All>
<ns7:SymmetricBindingxmlns:ns7="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<ns1:Policy>
<ns1:ExactlyOne>
<ns1:All>
<ns7:AlgorithmSuite>
<ns1:Policy>
<ns1:ExactlyOne>
<ns1:All>
<ns7:TripleDes />
</ns1:All>
</ns1:ExactlyOne>
</ns1:Policy>
</ns7:AlgorithmSuite>
<ns7:IncludeTimestamp />
<ns7:Layout>
<ns1:Policy>
<ns1:ExactlyOne>
<ns1:All>
<ns7:Strict />
</ns1:All>
</ns1:ExactlyOne>
</ns1:Policy>
</ns7:Layout>
<ns7:OnlySignEntireHeadersAndBody />
<ns7:ProtectionToken>
<ns1:Policy>
<ns1:ExactlyOne>
<ns1:All>
<ns7:X509Tokenns7:IncludeToken=
"http://schemas.xmlsoap.org/ws/2005/07/securitypolicy/IncludeToken/Never">
<ns1:Policy>
<ns1:ExactlyOne>
<ns1:All>
<ns7:WssX509V3Token10/>
</ns1:All>
</ns1:ExactlyOne>
</ns1:Policy>
</ns7:X509Token>
</ns1:All>
</ns1:ExactlyOne>
</ns1:Policy>
</ns7:ProtectionToken>
</ns1:All>
</ns1:ExactlyOne>
</ns1:Policy>
</ns7:SymmetricBinding>
<ns8:Wss11xmlns:ns8="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<ns1:Policy>
<ns1:ExactlyOne>
<ns1:All>
<ns8:MustSupportRefEncryptedKey />
<ns8:MustSupportRefIssuerSerial />
<ns8:MustSupportRefThumbprint />
</ns1:All>
</ns1:ExactlyOne>
</ns1:Policy>
</ns8:Wss11>
<sc:KeyStore wspp:visibility="private"
alias="xws-security-server"
storepass="changeit" type="JKS"
location="keystore.jks" />
<sc:TrustStore wspp:visibility="private"
peeralias="xws-security-client"
storepass="changeit" type="JKS"
location="cacerts.jks" />
<sc:ValidatorConfigurationxmlns:sc=
"http://schemas.sun.com/2006/03/wss/server">
<sc:Validator name="usernameValidator"
classname="com.tmax.UsernamePasswordValidator" />
</sc:ValidatorConfiguration>
<ns9:UsingAddressingxmlns:ns9="http://www.w3.org/2006/05/addressing/wsdl" />
</ns1:All>
</ns1:ExactlyOne>
</ns1:Policy>
<ns10:Policy xmlns:ns10="http://schemas.xmlsoap.org/ws/2004/09/policy"
wsu:Id="NewWebServicePortBinding_add_Input_Policy">
<ns10:ExactlyOne>
<ns10:All>
<ns11:EncryptedPartsxmlns:ns11=
"http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<ns11:Body />
</ns11:EncryptedParts>
<ns12:SignedPartsxmlns:ns12=
"http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<ns12:Body />
<ns12:Header Name="ReplyTo"
Namespace="http://www.w3.org/2005/08/addressing" />
<ns12:HeaderNamespace="http://www.w3.org/2005/08/addressing" Name="To"/>
<ns12:Header Name="From"
Namespace="http://www.w3.org/2005/08/addressing"/>
<ns12:Header Name="MessageId"
Namespace="http://www.w3.org/2005/08/addressing"/>
<ns12:Header Name="FaultTo"
Namespace="http://www.w3.org/2005/08/addressing"/>
<ns12:Header Name="Action"
Namespace="http://www.w3.org/2005/08/addressing"/>
<ns12:Header Name="RelatesTo"
Namespace="http://www.w3.org/2005/08/addressing"/>
</ns12:SignedParts>
<ns13:SignedSupportingTokensxmlns:ns13=
"http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<ns10:Policy>
<ns10:ExactlyOne>
<ns10:All>
<ns13:UsernameToken ns13:
IncludeToken="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy/
IncludeToken/AlwaysToRecipient">
<ns10:Policy>
<ns10:ExactlyOne>
<ns10:All>
<ns13:WssUsernameToken10/>
</ns10:All>
</ns10:ExactlyOne>
</ns10:Policy>
</ns13:UsernameToken>
</ns10:All>
</ns10:ExactlyOne>
</ns10:Policy>
</ns13:SignedSupportingTokens>
</ns10:All>
</ns10:ExactlyOne>
</ns10:Policy>
<ns14:Policy xmlns:ns14="http://schemas.xmlsoap.org/ws/2004/09/policy"
wsu:Id="NewWebServicePortBinding_add_Output_Policy">
<ns14:ExactlyOne>
<ns14:All>
<ns15:EncryptedPartsxmlns:ns15="http://schemas.xmlsoap.org/ws/
2005/07/securitypolicy">
<ns15:Body />
</ns15:EncryptedParts>
<ns16:SignedPartsxmlns:ns16="http://schemas.xmlsoap.org/ws/
2005/07/securitypolicy">
<ns16:Body />
<ns16:Header Name="ReplyTo"
Namespace="http://www.w3.org/2005/08/addressing"/>
<ns16:HeaderNamespace="http://www.w3.org/2005/08/addressing"
Name="To"/>
<ns16:Header Name="From"
Namespace="http://www.w3.org/2005/08/addressing"/>
<ns16:Header Name="MessageId"
Namespace="http://www.w3.org/2005/08/addressing"/>
<ns16:Header Name="FaultTo"
Namespace="http://www.w3.org/2005/08/addressing"/>
<ns16:Header Name="Action"
Namespace="http://www.w3.org/2005/08/addressing"/>
<ns16:Header Name="RelatesTo"
Namespace="http://www.w3.org/2005/08/addressing"/>
</ns16:SignedParts>
</ns14:All>
</ns14:ExactlyOne>
</ns14:Policy>
<types>
...
</types>
<message name="add">
...
</message>
<portType name="NewWebService">
...
</portType>
<binding name="NewWebServicePortBinding" type="tns:NewWebService">
<ns17:PolicyReferencexmlns:ns17="http://schemas.xmlsoap.org/ws/2004/09/policy"
URI="#NewWebServicePortBindingPolicy" />
<soap:binding transport="http://schemas.xmlsoap.org/soap/http" style="document" />
<operation name="add">
<soap:operation soapAction="" />
<input>
<ns18:PolicyReferencexmlns:ns18="http://schemas.xmlsoap.org/ws/2004/09/policy"
URI="#NewWebServicePortBinding_add_Input_Policy" />
<soap:body use="literal" />
</input>
<output>
<ns19:PolicyReferencexmlns:ns19="http://schemas.xmlsoap.org/ws/2004/09/policy"
URI="#NewWebServicePortBinding_add_Output_Policy" />
<soap:body use="literal" />
</output>
</operation>
</binding>
<service name="NewWebServiceService">
<port name="NewWebServicePort" binding="tns:NewWebServicePortBinding">
<soap:addresslocation="http://localhost:8088/usernameAuthentication_war/
NewWebServiceService"/>
</port>
</service>
</definitions>
For a web service client in which message security is configured, a keystore and a callback handler must be additionally configured in the wsit-client.xml file. Other message security settings are automatically configured by reading the message security policy from the server-side WSDL at runtime.
To set a keystore in the 'keystore-filename' element, set the path of the actual keystore file with an absolute or relative path. When using a relative path, the keystore file should be placed in the 'META-INF' directory under the 'classes' directory, which contains the service implementation classes.
[Example 17.14] << jeus-webservices-config.xsd >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<definitions xmlns="http://schemas.xmlsoap.org/wsdl/"
...
targetNamespace="http://server.fromjava/">
<wsp:UsingPolicy />
<wsp:Policy wsu:Id="TmaxBP0">
<wsp:ExactlyOne>
<wsp:All>
<CallbackHandlerConfiguration
xmlns="http://schemas.sun.com/2006/03/wss/client">
<CallbackHandler default="user_jeus" name="usernameHandler" />
<CallbackHandler default="password_jeus"
name="passwordHandler" />
</CallbackHandlerConfiguration>
<TrustStore location="cacerts.jks" peeralias="xws-security-server"
storepass="changeit" type="JKS"
xmlns:ns0="http://java.sun.com/xml/ns/wsit/policy"
ns0:visibility="private"
xmlns="http://schemas.sun.com/2006/03/wss/client" />
</wsp:All>
</wsp:ExactlyOne>
</wsp:Policy>
<types>
...
</types>
<message name="addNumbers">
...
</message>
<portType name="AddNumbersImpl">
...
</portType>
<binding name="AddNumbersImplPortBinding" type="tns:AddNumbersImpl">
<wsp:PolicyReference URI="#TmaxBP0" />
<soap:binding style="document"
transport="http://schemas.xmlsoap.org/soap/http" />
<operation name="addNumbers">
<soap:operation soapAction="" />
<input>
<soap:body use="literal" />
</input>
<output>
<soap:body use="literal" />
</output>
</operation>
</binding>
<service name="AddNumbersImplService">
<port binding="tns:AddNumbersImplPortBinding" name="AddNumbersImplPort">
<soap:address
location="http://localhost:8088/DocLitEchoService/AddNumbersImplService" />
</port>
</service>
</definitions>
This section describes how to improve symmetric binding through user name authentication for server and client applications.
There are two kinds of web service settings on the server side, the web service configuration file, 'service-config.xml', and username validator setting.
Creating Web Service Configuration File
The following is an example of creating a web service configuration file.
[Example 17.15] <<service-config.xml>>
<?xml version="1.0" encoding="UTF-8"?>
<web-services-config xmlns="http://www.tmaxsoft.com/xml/ns/jeus">
<policy>
<endpoint-policy-subject>
<security-policy>
<security-binding>
<symmetric-binding>
<protection-token>
<x509-token>
<include-token>true</include-token>
</x509-token>
</protection-token>
</symmetric-binding>
</security-binding>
<token>
<signed-supporting-token>
<username-token>
<username-password-validator>
fromjava.server.UsernamePasswordValidator
</username-password-validator>
<include-token>true</include-token>
</username-token>
</signed-supporting-token>
</token>
<protection>
<signed-part>...</signed-part>
<encrypted-part>...</encrypted-part>
</protection>
<wss-version>11</wss-version>
<keystore>...</keystore>
</security-policy>
</endpoint-policy-subject>
</policy>
</web-services-config>
Creating a Username Validator Class
Validate the username and password of the user who used a username token to access the service by implementing the class, com.sun.xml.wss.impl.callback.PasswordValidationCallback.PasswordValidator.
[Example 17.16] << UsernamePasswordValidator.java >>
public class UsernamePasswordValidator implements
PasswordValidationCallback.PasswordValidator {
public boolean validate(PasswordValidationCallback.Request request)
throws PasswordValidationCallback.PasswordValidationException {
...
return false;
}
private boolean validateUserFromDB(String username, String password) {
...
return false;
}
}
To configure a web service on the client side, a username handler and a keystore (truststore) must be configured in the wsit-client.xml file.
Setting a Keystore (Truststore) and a Username Handler
Configure the following settings in the wsit-client.xml file.
[Example 17.17] <<wsit-client.xml>>
<?xml version="1.0" encoding="UTF-8"?>
<definitions xmlns="http://schemas.xmlsoap.org/wsdl/"
...
targetNamespace="http://server.fromjava/">
<wsp:UsingPolicy />
<wsp:Policy wsu:Id="TmaxBP0">
<wsp:ExactlyOne>
<wsp:All>
<CallbackHandlerConfiguration
xmlns="http://schemas.sun.com/2006/03/wss/client">
<CallbackHandler default="user_jeus" name="usernameHandler" />
<CallbackHandler default="password_jeus"
name="passwordHandler" />
</CallbackHandlerConfiguration>
<TrustStore location="cacerts.jks" peeralias="xws-security-server"
storepass="changeit" type="JKS"
xmlns:ns0="http://java.sun.com/xml/ns/wsit/policy"
ns0:visibility="private"
xmlns="http://schemas.sun.com/2006/03/wss/client" />
</wsp:All>
</wsp:ExactlyOne>
</wsp:Policy>
...
<binding name="AddNumbersImplPortBinding" type="tns:AddNumbersImpl">
<wsp:PolicyReference URI="#TmaxBP0" />
...
</binding>
...
</definitions>
Creating a username handler class
Various settings can be configured by implementing the javax.security.auth.callback.CallbackHandler interface and transmitting each Callback to the CallbackHandler. The settings are configured according to the policy of the transmitted callback type.
The CallbackHandler interface sets a username and password for the callback by using the transmitted callbacks, NameCallback and PasswordCallback, from the previous example. In the following example, a username and password are already specified in the class file, but the user can also enter the values using various reader objects as needed.
[Example 17.18] << UsernamePasswordCallbackHandler.java >>
public class UsernamePasswordCallbackHandler implements CallbackHandler {
public void handle(Callback[] callbacks) throws IOException,
UnsupportedCallbackException {
for (int i = 0; i < callbacks.length; i++) {
Callback callback = callbacks[i];
if (callback instanceof NameCallback) {
((NameCallback) callback).setName("user_jeus");
} else if (callback instanceof PasswordCallback) {
((PasswordCallback) callback).setPassword((
new String("password_jeus")).toCharArray());
} else {
throw new UnsupportedCallbackException(callback,
"Unknow callback for username or password");
}
}
}
}
This section explains how to configure mutual certificates security in the server and client applications.
A web service on the server side can be configured in the 'service-config.xml', the web service configuration file.
[Example 17.19] << service-config.xml >>
<?xml version="1.0" encoding="UTF-8"?>
<web-services-config xmlns="http://www.tmaxsoft.com/xml/ns/jeus">
<policy>
<endpoint-policy-subject>
<security-policy>
<security-binding>
<asymmetric-binding>
<initiator-token>
<x509-token>
<include-token>true</include-token>
</x509-token>
</initiator-token>
<recipient-token>
<x509-token>
<include-token>false</include-token>
</x509-token>
</recipient-token>
</asymmetric-binding>
</security-binding>
<protection>
<signed-part>...</signed-part>
<encrypted-part>...</encrypted-part>
</protection>
<keystore>...</keystore>
<truststore>...</truststore>
</security-policy>
</endpoint-policy-subject>
</policy>
</web-services-config>
To configure a client-side web service, a keystore (truststore) must also be configured in the wsit-client.xml file.
[Example 17.20] << wsit-client.xml >>
<?xml version="1.0" encoding="UTF-8"?>
<definitions xmlns="http://schemas.xmlsoap.org/wsdl/"
...
targetNamespace="http://server.fromjava/">
<wsp:UsingPolicy/>
<wsp:Policy wsu:Id="TmaxBP0">
<wsp:ExactlyOne>
<wsp:All>
<KeyStore
alias="xws-security-client"
location="keystore.jks"
storepass="changeit" type="JKS"
xmlns:ns0="http://java.sun.com/xml/ns/wsit/policy"
ns0:visibility="private"
xmlns="http://schemas.sun.com/2006/03/wss/client"/>
<TrustStore
location="cacerts.jks"
peeralias="xws-security-server"
storepass="changeit"
type="JKS"
xmlns:ns0="http://java.sun.com/xml/ns/wsit/policy"
ns0:visibility="private"
xmlns="http://schemas.sun.com/2006/03/wss/client"/>
</wsp:All>
</wsp:ExactlyOne>
</wsp:Policy>
...
<binding name="AddNumbersImplPortBinding" type="tns:AddNumbersImpl">
<wsp:PolicyReference URI="#TmaxBP0"/>
...
</binding>
...
</definitions>
This section describes how to configure an SSL-based SAML authentication on the server and client.
The server-side web service settings can be configured in the 'service-config.xml', the web service configuration file.
[Example 17.21] << service-config.xml >>
<?xml version="1.0" encoding="UTF-8"?>
<web-services-config xmlns="http://www.tmaxsoft.com/xml/ns/jeus">
<policy>
<endpoint-policy-subject>
<security-policy>
<security-binding>
<transport-binding>
<transport-token>
<https-token/>
</transport-token>
</transport-binding>
</security-binding>
</security-policy>
<operation-policy-subject>
<operation-java-name>addNumbers</operation-java-name>
<input-message-policy-subject>
<security-policy>
<supporting-token>
<signed-supporting-token>
<saml-token>
</saml-token>
</signed-supporting-token>
</supporting-token>
</security-policy>
</input-message-policy-subject>
</operation-policy-subject>
</endpoint-policy-subject>
</policy>
</web-services-config>
For the client-side web service settings, a handler class of the SAML message must be additionally configured in the wsit-client.xml file.
Setting a Handler Class to Process SAML Messages
Configure a handler class to process SAML messages in wsit-client.xml as in the following example.
[Example 17.22] << wsit-client.xml >>
<?xml version="1.0" encoding="UTF-8"?>
<definitions xmlns="http://schemas.xmlsoap.org/wsdl/"
...
targetNamespace="http://server.fromjava/">
<ns5:Policy xmlns:ns5="http://schemas.xmlsoap.org/ws/2004/09/policy"
wsu:Id="TmaxBO1TmaxIn1">
<ns5:ExactlyOne>
<ns5:All>
<CallbackHandlerConfiguration
xmlns="http://schemas.sun.com/2006/03/wss/client">
<CallbackHandler classname="xwss.saml.SamlCallbackHandler"
name="samlHandler" />
</CallbackHandlerConfiguration>
</ns5:All>
</ns5:ExactlyOne>
</ns5:Policy>
...
<binding name="AddNumbersImplPortBinding" type="tns:AddNumbersImpl">
...
<operation name="addNumbers">
<soap:operation soapAction="" />
<input>
<ns10:PolicyReference
xmlns:ns10="http://schemas.xmlsoap.org/ws/2004/09/policy"
URI="#TmaxBO1TmaxIn1" />
<soap:body use="literal" />
</input>
<output>
<soap:body use="literal" />
</output>
</operation>
</binding>
...
</definitions>
Creating a Handler Class to Process SAML Messages
In order to include information in the SOAP request message according to the SAML standard, the example uses SamlCallbackHandler class which implements javax.security.auth.callback.CallbackHandler. SamlCallbackHandler stores the required assertions according to the callback type.
The following is the SamlCallbackHandler class used in the example.
[Example 17.23] << SamlCallbackHandler.java >>
public class SamlCallbackHandler implements CallbackHandler {
...
public void handle(Callback[] callbacks) throws IOException,
UnsupportedCallbackException {
for (int i = 0; i < callbacks.length; i++) {
if (callbacks[i] instanceof SAMLCallback) {
try {
SAMLCallback samlCallback = (SAMLCallback) callbacks[i];
if (samlCallback.getConfirmationMethod().equals(
samlCallback.SV_ASSERTION_TYPE)) {
samlCallback.setAssertionElement(createSVSAMLAssertion());
svAssertion = samlCallback.getAssertionElement();
} else if (samlCallback.getConfirmationMethod().equals(
samlCallback.HOK_ASSERTION_TYPE)) {
samlCallback.setAssertionElement(createHOKSAMLAssertion());
hokAssertion = samlCallback.getAssertionElement();
} else {
throw new Exception("SAML Assertion Type is not matched.");
}
} catch (Exception ex) {
ex.printStackTrace();
}
} else {
throw unsupported;
}
}
}
private static Element createSVSAMLAssertion() {...}
private static Element createSVSAMLAssertion20() {...}
private Element createHOKSAMLAssertion() {...}
private Element createHOKSAMLAssertion20() {...}
...
}
This section describes how to configure secure conversation in server and client applications.
The server-side web service is configured through the service-config.xml web service configuration file.
[Example 17.24] <<service-config.xml>>
<?xml version="1.0" encoding="UTF-8"?>
<web-services-config xmlns="http://www.tmaxsoft.com/xml/ns/jeus">
<policy>
<endpoint-policy-subject>
<portcomponent-wsdl-name>AddNumbersPort</portcomponent-wsdl-name>
<addressing-policy>
<www-w3-org />
</addressing-policy>
<security-policy>
<security-binding>
<symmetric-binding>
<protection-token>
<secure-conversation-token>
<asymmetric-binding-initiator-token>
<include-token>true</include-token>
</asymmetric-binding-initiator-token>
<asymmetric-binding-recipient-token>
</asymmetric-binding-recipient-token>
<include-token>true</include-token>
</secure-conversation-token>
</protection-token>
<encrypt-signature>true</encrypt-signature>
</symmetric-binding>
</security-binding>
<trust>true</trust>
<keystore>...</keystore>
<truststore>...</truststore>
</security-policy>
<operation-policy-subject>
<operation-wsdl-name>addNumbers</operation-wsdl-name>
<input-message-policy-subject>
<security-policy>
<protection>
<signed-part>...</signed-part>
<encrypted-part>...</encrypted-part>
</protection>
</security-policy>
</input-message-policy-subject>
</operation-policy-subject>
</endpoint-policy-subject>
</policy>
</web-services-config>
To configure a client-side web service, a keystore (truststore) must also be configured in the wsit-client.xml file.
[Example 17.25] <<wsit-client.xml>>
<?xml version="1.0" encoding="UTF-8"?>
<definitions xmlns="http://schemas.xmlsoap.org/wsdl/"
...
xmlns:soap12="http://schemas.xmlsoap.org/wsdl/soap12/">
<message name="add" />
<message name="addResponse" />
<portType name="NewWebService">
<wsdl:operation name="add">
<wsdl:input message="tns:add" />
<wsdl:output message="tns:addResponse" />
</wsdl:operation>
</portType>
<binding name="NewWebServicePortBinding" type="tns:NewWebService">
<wsp:PolicyReference URI="#NewWebServicePortBindingPolicy" />
<soap12:binding style="document"
transport="http://schemas.xmlsoap.org/soap/http" />
<wsdl:operation name="add">
<soap12:operation soapAction="http://xmlsoap.org/Ping"
style="document" />
<wsdl:input>
<soap12:body use="literal" />
</wsdl:input>
<wsdl:output>
<soap12:body use="literal" />
</wsdl:output>
</wsdl:operation>
</binding>
<service name="NewWebServiceService">
<wsdl:port name="NewWebServicePort" binding="tns:NewWebServicePortBinding">
<soap12:address location="REPLACE_WITH_ACTUAL_ADDRESS" />
</wsdl:port>
</service>
<wsp:Policy wsu:Id="NewWebServicePortBindingPolicy"
xmlns:scc="http://schemas.sun.com/ws/2006/05/sc/client">
<wsp:ExactlyOne>
<wsp:All>
<sc:KeyStore wspp:visibility="private"
location="./keystore.jks" type="JKS"
alias="xws-security-client" storepass="changeit">
</sc:KeyStore>
<sc:TrustStore wspp:visibility="private"
location="./cacerts.jks" type="JKS"
storepass="changeit" peeralias="xws-security-server"
stsalias="wssip">
</sc:TrustStore>
<scc:SCClientConfiguration wspp:visibility="private">
<scc:LifeTime>36000</scc:LifeTime>
</scc:SCClientConfiguration>
</wsp:All>
</wsp:ExactlyOne>
</wsp:Policy>
</definitions>
This section describes how to configure a server, STS, and client for WS-Trust.
The server-side web service is configured in the 'service-config.xml', the web service configuration file.
[Example 17.26] <<service-config.xml>>
<?xml version="1.0" encoding="UTF-8"?>
<web-services-config xmlns="http://www.tmaxsoft.com/xml/ns/jeus">
<policy>
<endpoint-policy-subject>
<!--
Web service trust runs on the WS-Addressing framework.
-->
<addressing-policy>
<www-w3-org />
</addressing-policy>
<security-policy>
<!--
Specify that the Web service will use the x509 token as security token.
-->
<security-binding>
<symmetric-binding>
<protection-token>
<x509-token />
</protection-token>
<layout>Strict</layout>
</symmetric-binding>
</security-binding>
<!--
Specify that an additional security token for the Web service should be issued by STS of the following.
-->
<token>
<endorsing-supporting-token>
<issued-token>
<issuer-address>
http://localhost:8088/trust_sts/SecurityTokenService
</issuer-address>
</issued-token>
</endorsing-supporting-token>
</token>
<wss-version>11</wss-version>
<trust>true</trust>
...
</security-policy>
...
</endpoint-policy-subject>
</policy>
</web-services-config>
For STS configuration, the WS-SecurityPolicy must be configured through the WS-Policy framework of WSDL.
The following is an example of configuring the WS-SecurityPolicy.
[Example 17.27] WS-SecurityPolicy Setting : <<sts.wsdl>>
<?xml version="1.0" encoding="UTF-8"?>
<wsdl:definitions ...>
<wsp:Policy wsu:Id="TmaxSTSServerPolicy">
<wsp:ExactlyOne>
<wsp:All>
<sp:SymmetricBinding
xmlns:sp="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<wsp:Policy>
<sp:ProtectionToken>
<wsp:Policy>
<sp:X509Token sp:
IncludeToken="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy/IncludeToken/Never">
<wsp:Policy>
<sp:RequireDerivedKeys />
<sp:RequireThumbprintReference />
<sp:WssX509V3Token10 />
</wsp:Policy>
</sp:X509Token>
</wsp:Policy>
</sp:ProtectionToken>
<sp:AlgorithmSuite>
<wsp:Policy>
<sp:Basic128 />
</wsp:Policy>
</sp:AlgorithmSuite>
<sp:Layout>
<wsp:Policy>
<sp:Lax />
</wsp:Policy>
</sp:Layout>
<sp:IncludeTimestamp />
<sp:EncryptSignature />
<sp:OnlySignEntireHeadersAndBody />
</wsp:Policy>
</sp:SymmetricBinding>
<sp:SignedSupportingTokens
xmlns:sp="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<wsp:Policy>
<sp:UsernameToken sp:
IncludeToken="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy/IncludeToken/AlwaysToRecipient">
<wsp:Policy>
<sp:WssUsernameToken10 />
</wsp:Policy>
</sp:UsernameToken>
</wsp:Policy>
</sp:SignedSupportingTokens>
<sp:Wss11
xmlns:sp="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<wsp:Policy>
<sp:MustSupportRefKeyIdentifier />
<sp:MustSupportRefIssuerSerial />
<sp:MustSupportRefThumbprint />
<sp:MustSupportRefEncryptedKey />
</wsp:Policy>
</sp:Wss11>
<sp:Trust10
xmlns:sp="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<wsp:Policy>
<sp:MustSupportIssuedTokens />
<sp:RequireClientEntropy />
<sp:RequireServerEntropy />
</wsp:Policy>
</sp:Trust10>
...
<sc:ValidatorConfiguration
xmlns:sc="http://schemas.sun.com/2006/03/wss/server">
<sc:Validator name="usernameValidator"
classname="trust.sts.UsernamePasswordValidator" />
</sc:ValidatorConfiguration>
<tc:STSConfiguration
xmlns:tc="http://schemas.sun.com/ws/2006/05/trust/server"
encryptIssuedKey="true" encryptIssuedToken="false">
<tc:LifeTime>36000</tc:LifeTime>
<tc:Contract>
com.sun.xml.ws.security.trust.impl.IssueSamlTokenContractImpl
</tc:Contract>
<tc:Issuer>TmaxsoftSTS</tc:Issuer>
<tc:ServiceProviders>
<tc:ServiceProviderendPoint="http://localhost:8088/trust_server/FinancialService">
<tc:CertAlias>bob</tc:CertAlias>
<tc:TokenType>
http://docs.oasis-open.org/wss/oasis-wss-saml-token-profile-1.1#SAMLV1.1
</tc:TokenType>
</tc:ServiceProvider>
<tc:ServiceProvider endPoint="default">
<tc:CertAlias>bob</tc:CertAlias>
<tc:TokenType>
http://docs.oasis-open.org/wss/oasis-wss-saml-token-profile-1.1#SAMLV1.1
</tc:TokenType>
</tc:ServiceProvider>
</tc:ServiceProviders>
</tc:STSConfiguration>
<wsap10:UsingAddressing />
</wsp:All>
</wsp:ExactlyOne>
</wsp:Policy>
...
<wsdl:binding name="ISecurityTokenService_Binding"
type="tns:ISecurityTokenService">
<wsp:PolicyReference URI="#TmaxSTSServerPolicy" />
...
</wsdl:binding>
...
</wsdl:definitions>
To configure a client-side web service, a keystore (truststore) for each server and STS must be configured in the wsit-client.xml file.
[Example 17.28] <<wsit-client.xml>>
<?xml version="1.0" encoding="UTF-8"?>
<wsdl:definitions targetNamespace="http://tempuri.org/" ...>
<!-- FinancialService WSDL -->
<wsp:Policy wsu:Id="TmaxFSClientPolicy" ...>
<wsp:ExactlyOne>
<wsp:All>
<sc:KeyStore ... />
<sc:TrustStore ... />
<scc:SCClientConfiguration wspp:visibility="private">
<scc:LifeTime>36000</scc:LifeTime>
</scc:SCClientConfiguration>
</wsp:All>
</wsp:ExactlyOne>
</wsp:Policy>
...
<wsdl:binding name="IFinancialService_Binding"
type="tns:IFinancialService">
<wsp:PolicyReference URI="#TmaxFSClientPolicy" />
...
</wsdl:binding>
<wsdl:service name="FinancialService">
<wsdl:port name="IFinancialService_Port"
binding="tns:IFinancialService_Binding">
<soap:address
location="http://localhost:8088/trust_server/FinancialService" />
</wsdl:port>
</wsdl:service>
<!-- STSService WSDL -->
<wsp:Policy wsu:Id="TmaxSTSClientPolicy" ...>
<wsp:ExactlyOne>
<wsp:All>
<sc:KeyStore ... />
<sc:TrustStore ... />
<sc:CallbackHandlerConfiguration
xmlns:sc="http://schemas.sun.com/2006/03/wss/client">
<sc:CallbackHandler default="alice" name="usernameHandler" />
<sc:CallbackHandler default="alice" name="passwordHandler" />
</sc:CallbackHandlerConfiguration>
</wsp:All>
</wsp:ExactlyOne>
</wsp:Policy>
...
<wsdl:binding name="ISecurityTokenService_Binding"
type="tns:ISecurityTokenService">
<wsp:PolicyReference URI="#TmaxSTSClientPolicy" />
...
</wsdl:binding>
<wsdl:service name="SecurityTokenService">
<wsdl:port name="ISecurityTokenService_Port"
binding="tns:ISecurityTokenService_Binding">
<soap:address
location="http://localhost:8088/trust_sts/STSImplService" />
</wsdl:port>
</wsdl:service>
</wsdl:definitions>
The following is an example of executing a client.
<<__Exception__>> com.sun.xml.ws.server.UnsupportedMediaException: Unsupported Content-Type: application/soap+xml Supported ones are: [text/xml] at com.sun.xml.ws.encoding.StreamSOAPCodec.decode(StreamSOAPCodec.java:295) at com.sun.xml.ws.encoding.StreamSOAPCodec.decode(StreamSOAPCodec.java:129) at com.sun.xml.ws.encoding.SOAPBindingCodec.decode(SOAPBindingCodec.java:287) at jeus.webservices.jaxws.transport.http.HttpAdapter.decodePacket (HttpAdapter.java:322) at jeus.webservices.jaxws.transport.http.HttpAdapter.access$3 (HttpAdapter.java:287) at jeus.webservices.jaxws.transport.http.HttpAdapter$HttpToolkit.handle (HttpAdapter.java:517) at jeus.webservices.jaxws.transport.http.HttpAdapter.handle (HttpAdapter.java:272) at jeus.webservices.jaxws.transport.http.EndpointAdapter.handle (EndpointAdapter.java:149) at jeus.webservices.jaxws.transport.http.servlet.WSServletDelegate.doGet (WSServletDelegate.java:139) at jeus.webservices.jaxws.transport.http.servlet.WSServletDelegate.doPost (WSServletDelegate.java:170) at jeus.webservices.jaxws.transport.http.servlet.WSServlet.doPost (WSServlet.java:23) at javax.servlet.http.HttpServlet.service(HttpServlet.java:725) at javax.servlet.http.HttpServlet.service(HttpServlet.java:818) at jeus.servlet.engine.ServletWrapper.executeServlet(ServletWrapper.java:328) at jeus.servlet.engine.ServletWrapper.execute(ServletWrapper.java:222) at jeus.servlet.engine.HttpRequestProcessor.run(HttpRequestProcessor.java:278) <<__!Exception__>> [2999.01.01 00:00:00][0][bxxx] [TMAX-xx] Unsupported Content-Type: application/soap+xml Supported ones are: [text/xml] <<__Exception__>> com.sun.xml.ws.server.UnsupportedMediaException: Unsupported Content-Type: application/soap+xml Supported ones are: [text/xml] at com.sun.xml.ws.encoding.StreamSOAPCodec.decode(StreamSOAPCodec.java:295) at com.sun.xml.ws.encoding.StreamSOAPCodec.decode(StreamSOAPCodec.java:129) at com.sun.xml.ws.encoding.SOAPBindingCodec.decode(SOAPBindingCodec.java:287) at jeus.webservices.jaxws.transport.http.HttpAdapter.decodePacket (HttpAdapter.java:322) at jeus.webservices.jaxws.transport.http.HttpAdapter.access$3 (HttpAdapter.java:287) at jeus.webservices.jaxws.transport.http.HttpAdapter$HttpToolkit.handle (HttpAdapter.java:517) at jeus.webservices.jaxws.transport.http.HttpAdapter.handle(HttpAdapter.java:272) at jeus.webservices.jaxws.transport.http.EndpointAdapter.handle (EndpointAdapter.java:149) at jeus.webservices.jaxws.transport.http.servlet.WSServletDelegate.doGet (WSServletDelegate.java:139) at jeus.webservices.jaxws.transport.http.servlet.WSServletDelegate.doPost (WSServletDelegate.java:170) at jeus.webservices.jaxws.transport.http.servlet.WSServlet.doPost (WSServlet.java:23) at javax.servlet.http.HttpServlet.service(HttpServlet.java:725) at javax.servlet.http.HttpServlet.service(HttpServlet.java:818) at jeus.servlet.engine.ServletWrapper.executeServlet(ServletWrapper.java:328) at jeus.servlet.engine.ServletWrapper.execute(ServletWrapper.java:222) at jeus.servlet.engine.HttpRequestProcessor.run(HttpRequestProcessor.java:278) <<__!Exception__>> user alice is a validate user. your company : Tmaxsoft your department : Infra
Once the client is executed, the client attempts to connect through various URL suffixes in order to get the STS URL information. If the log level is set to a value higher than 'FINE', the exception in the previous example will occur.
As mentioned already, the message-level security in JEUS web services works through the web service security policy. The web service security policy can be directly set in the WSDL document or wsit-endpoint.xml file.
The web service policy can be configured in the service-config.xml file, which supports the web service security policy. If the service-config.xml file can be shared between the server and client, any user can easily process message-level security on both sides by using the file, without understanding the web service and web service security policies. This is similar to the message-level security for the JAX-RPC (JEUS 5) web service.
The encryption settings for the message-level security in JAX-RPC (JEUS 5) web services are divided into the following.
-
Configuring JAX-RPC web services
-
Configuring JAX-WS web services
Configuring JAX-RPC Web Services
The encryption settings for the message-level security in JAX-RPC web services are configured in the jeuswebservices- dd.xml file (servers) or the jeus-web-dd.xml file (client), as shown in the following example.
[Example 17.29] << jeus-webservices-dd.xml >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<jeus-webservices-dd xmlns="http://www.tmaxsoft.com/xml/ns/jeus">
<service>
<webservice-description-name>
PingSecurityService
</webservice-description-name>
<port>
<port-component-name>PingPort</port-component-name>
<security>
<request-receiver>
<action-list>Encrypt</action-list>
<password-callback-class>
ping.PingPWCallback
</password-callback-class>
<decryption>
<keystore>
<key-type>jks</key-type>
<keystore-password>changeit</keystore-password>
<keystore-filename>
server-keystore.jks
</keystore-filename>
</keystore>
</decryption>
</request-receiver>
<response-sender>
<action-list>Encrypt</action-list>
<password-callback-class>
ping.PingPWCallback
</password-callback-class>
<encryption-infos>
<encryption-info>
<encryptionUser>xws-security-client</encryptionUser>
<keyIdentifier>DirectReference</keyIdentifier>
<keystore>
<key-type>jks</key-type>
<keystore-password>changeit</keystore-password>
<keystore-filename>
server-truststore.jks
</keystore-filename>
</keystore>
</encryption-info>
</encryption-infos>
</response-sender>
</security>
</port>
</service>
</jeus-webservices-dd>
Configuring JAX-WS(JEUS 8) Web Services
The encryption settings for the message-level security in JAX-WS (JEUS 8) web services are configured by adding the service-config.xml file as the '-policy' option argument when creating a web service with the wsgen or wsimport tool.
[Example 17.30] << service-config.xml >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<web-services-config xmlns="http://www.tmaxsoft.com/xml/ns/jeus">
<policy>
<endpoint-policy-subject>
<portcomponent-wsdl-name>PingPort</portcomponent-wsdl-name>
<security-policy>
<security-binding>
<asymmetric-binding>
<initiator-token>
<x509-token/>
</initiator-token>
<recipient-token>
<x509-token/>
</recipient-token>
</asymmetric-binding>
</security-binding>
<keystore>
<keystore-file>
<alias>xws-security-client</alias>
<key-type>JKS</key-type>
<keystore-password>changeit</keystore-password>
<keystore-filename>
client-keystore.jks
</keystore-filename>
</keystore-file>
</keystore>
<truststore>
<keystore-file>
<alias>xws-security-server</alias>
<key-type>JKS</key-type>
<keystore-password>changeit</keystore-password>
<keystore-filename>
client-truststore.jks
</keystore-filename>
</keystore-file>
</truststore>
</security-policy>
<operation-policy-subject>
<operation-wsdl-name>ping</operation-wsdl-name>
<input-message-policy-subject>
<security-policy>
<protection>
<encrypted-part>
<body/>
</encrypted-part>
</protection>
</security-policy>
</input-message-policy-subject>
<output-message-policy-subject>
<security-policy>
<protection>
<encrypted-part>
<body/>
</encrypted-part>
</protection>
</security-policy>
</output-message-policy-subject>
</operation-policy-subject>
</endpoint-policy-subject>
</policy>
</web-services-config>
Signature settings for message-level security is divided into the following.
-
Configuring JAX-RPC web services
-
Configuring JAX-WS web services
Configuring JAX-RPC web services
The signature settings for the message-level security in JAX-RPC (JEUS 5) web services are configured in the jeuswebservices- dd.xml file (server) or the jeus-web-dd.xml file (client), as shown in the following.
[Example 17.31] << jeus-webservices-dd.xml >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<jeus-webservices-dd xmlns="http://www.tmaxsoft.com/xml/ns/jeus">
<service>
<webservice-description-name>
PingSecurityService
</webservice-description-name>
<port>
<port-component-name>PingPort</port-component-name>
<security>
<request-receiver>
<action-list>Signature</action-list>
<password-callback-class>
ping.PingPWCallback
</password-callback-class>
<signature-verification>
<keystore>
<key-type>jks</key-type>
<keystore-password>changeit</keystore-password>
<keystore-filename>
server-truststore.jks
</keystore-filename>
</keystore>
</signature-verification>
</request-receiver>
<response-sender>
<action-list>Signature</action-list>
<password-callback-class>
ping.PingPWCallback
</password-callback-class>
<user>xws-security-server</user>
<signature-infos>
<signature-info>
<keyIdentifier>DirectReference</keyIdentifier>
<keystore>
<key-type>jks</key-type>
<keystore-password>changeit</keystore-password>
<keystore-filename>
server-keystore.jks
</keystore-filename>
</keystore>
</signature-info>
</signature-infos>
</response-sender>
</security>
</port>
</service>
</jeus-webservices-dd>
Configuring JAX-WS web services
The message-level security in JAX-WS web services is configured by including the 'service-config.xml' as the '-policy' option argument when creating a web service by using the wsgen or wsimport tool.
[Example 17.32] << service-config.xml >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<web-services-config xmlns="http://www.tmaxsoft.com/xml/ns/jeus">
<policy>
<endpoint-policy-subject>
<portcomponent-wsdl-name>PingPort</portcomponent-wsdl-name>
<security-policy>
<security-binding>
<asymmetric-binding>
<initiator-token>
<x509-token/>
</initiator-token>
<recipient-token>
<x509-token/>
</recipient-token>
</asymmetric-binding>
</security-binding>
<keystore>
<keystore-file>
<alias>xws-security-client</alias>
<key-type>JKS</key-type>
<keystore-password>changeit</keystore-password>
<keystore-filename>
client-keystore.jks
</keystore-filename>
</keystore-file>
</keystore>
<truststore>
<keystore-file>
<alias>xws-security-server</alias>
<key-type>JKS</key-type>
<keystore-password>changeit</keystore-password>
<keystore-filename>
client-truststore.jks
</keystore-filename>
</keystore-file>
</truststore>
</security-policy>
<operation-policy-subject>
<operation-wsdl-name>ping</operation-wsdl-name>
<input-message-policy-subject>
<security-policy>
<protection>
<signed-part>
<body/>
</signed-part>
</protection>
</security-policy>
</input-message-policy-subject>
<output-message-policy-subject>
<security-policy>
<protection>
<signed-part>
<body/>
</signed-part>
</protection>
</security-policy>
</output-message-policy-subject>
</operation-policy-subject>
</endpoint-policy-subject>
</policy>
</web-services-config>
Timestamp settings for message-level security is divided into the following.
-
Configuring JAX-RPC web services
-
Configuring JAX-WS web services
Configuring JAX-RPC(JEUS 5) web services
The timestamp settings for the message-level security in JAX-RPC (JEUS 5) web services are configured in the jeus-webservicesdd.xml file (server) or the jeus-web-dd.xml file (client), as shown in the following example.
[Example 17.33] << jeus-webservices-dd.xml >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<jeus-webservices-dd xmlns="http://www.tmaxsoft.com/xml/ns/jeus">
<service>
<webservice-description-name>
PingSecurityService
</webservice-description-name>
<port>
<port-component-name>PingPort</port-component-name>
<security>
<request-receiver>
<action-list>Signature Timestamp</action-list>
<password-callback-class>
ping.PingPWCallback
</password-callback-class>
<signature-verification>
<keystore>
<key-type>jks</key-type>
<keystore-password>changeit</keystore-password>
<keystore-filename>
server-truststore.jks
</keystore-filename>
</keystore>
</signature-verification>
</request-receiver>
<response-sender>
<action-list>Signature</action-list>
<password-callback-class>
ping.PingPWCallback
</password-callback-class>
<user>xws-security-server</user>
<signature-infos>
<signature-info>
<keyIdentifier>DirectReference</keyIdentifier>
<keystore>
<key-type>jks</key-type>
<keystore-password>changeit</keystore-password>
<keystore-filename>
server-keystore.jks
</keystore-filename>
</keystore>
</signature-info>
</signature-infos>
</response-sender>
</security>
</port>
</service>
</jeus-webservices-dd>
Configuring JAX-WS(JEUS 8) web services
The message-level security in JAX-WS (JEUS 8) web services is configured by including the 'service-config.xml' as the '-policy' option argument when creating a web service by using the wsgen or wsimport tool.
[Example 17.34] << service-config.xml >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<web-services-config xmlns="http://www.tmaxsoft.com/xml/ns/jeus">
<policy>
<endpoint-policy-subject>
<portcomponent-wsdl-name>PingPort</portcomponent-wsdl-name>
<security-policy>
<security-binding>
<asymmetric-binding>
<initiator-token>
<x509-token/>
</initiator-token>
<recipient-token>
<x509-token/>
</recipient-token>
</asymmetric-binding>
<timestamp>true</timestamp>
</security-binding>
<keystore>
<keystore-file>
<alias>xws-security-client</alias>
<key-type>JKS</key-type>
<keystore-password>changeit</keystore-password>
<keystore-filename>
client-keystore.jks
</keystore-filename>
</keystore-file>
</keystore>
<truststore>
<keystore-file>
<alias>xws-security-server</alias>
<key-type>JKS</key-type>
<keystore-password>changeit</keystore-password>
<keystore-filename>
client-truststore.jks
</keystore-filename>
</keystore-file>
</truststore>
</security-policy>
<operation-policy-subject>
<operation-wsdl-name>ping</operation-wsdl-name>
<input-message-policy-subject>
<security-policy>
<protection>
<signed-part>
<body/>
</signed-part>
</protection>
</security-policy>
</input-message-policy-subject>
<output-message-policy-subject>
<security-policy>
<protection>
<signed-part>
<body/>
</signed-part>
</protection>
</security-policy>
</output-message-policy-subject>
</operation-policy-subject>
</endpoint-policy-subject>
</policy>
</web-services-config>
Username token settings for message-level security is divided into the following.
-
Configuring JAX-RPC web services
-
Configuring JAX-WS web services
Configuring JAX-RPC(JEUS 5) web services
The username token settings for message-level security in JAX-RPC web services are configured in the jeus-webservices-dd.xml file (server) or the jeus-web-dd.xml file (clients), as shown in the following example.
[Example 17.35] << jeus-webservices-dd.xml >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<jeus-webservices-dd xmlns="http://www.tmaxsoft.com/xml/ns/jeus">
<service>
<webservice-description-name>
PingSecurityService
</webservice-description-name>
<port>
<port-component-name>PingPort</port-component-name>
<security>
<request-receiver>
<action-list>Signature UsernameToken</action-list>
<password-callback-class>
ping.PingPWCallback
</password-callback-class>
<signature-verification>
<keystore>
<key-type>jks</key-type>
<keystore-password>changeit</keystore-password>
<keystore-filename>
server-truststore.jks
</keystore-filename>
</keystore>
</signature-verification>
</request-receiver>
<response-sender>
<action-list>Signature UsernameToken</action-list>
<user>xws-security-server</user>
<password-callback-class>
ping.PingPWCallback
</password-callback-class>
<signature-infos>
<signature-info>
<keyIdentifier>DirectReference</keyIdentifier>
<keystore>
<key-type>jks</key-type>
<keystore-password>changeit</keystore-password>
<keystore-filename>
server-keystore.jks
</keystore-filename>
</keystore>
</signature-info>
</signature-infos>
</response-sender>
</security>
</port>
</service>
</jeus-webservices-dd>
Configuring JAX-WS(JEUS 8) web services
The message-level security in JAX-WS (JEUS 8) web services is configured by including the 'service-config.xml' as the '-policy' option argument when creating a web service by using the wsgen or wsimport tool.
[Example 17.36] << service-config.xml >>
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<web-services-config xmlns="http://www.tmaxsoft.com/xml/ns/jeus">
<policy>
<endpoint-policy-subject>
<security-policy>
<security-binding>
<symmetric-binding>
<protection-token>
<x509-token>
<include-token>true</include-token>
</x509-token>
</protection-token>
</symmetric-binding>
</security-binding>
<token>
<signed-supporting-token>
<username-token>
<username-password-validator>
fromjava.server.UsernamePasswordValidator
</username-password-validator>
<include-token>true</include-token>
</username-token>
</signed-supporting-token>
</token>
<keystore>
<keystore-file>
<alias>xws-security-server</alias>
<key-type>JKS</key-type>
<keystore-password>changeit</keystore-password>
<keystore-filename>
keystore.jks
</keystore-filename>
</keystore-file>
</keystore>
<wss-version>11</wss-version>
<protection>
<signed-part>
<body/>
</signed-part>
<encrypted-part>
<body/>
</encrypted-part>
</protection>
</security-policy>
</endpoint-policy-subject>
</policy>
</web-services-config>
Access control can be set for a JEUS web service to only allow users with permissions to invoke the web service, and the setting is different for each web service back-end. Access control can be set in the same way as described in the "27.4. Configuring Access Control" section, except for the method for invoking the client.
Portable artifacts must be created based on the information in WSDL in order to invoke a web service with access control settings (basic authentication). If a username and password is required for the service, they must also be configured.
Portable artifacts must be created for the clients of an access-controlled web service.
Enter the following command in the console to create portable artifacts by using the wsimport tool.
$ wsimport -Xauthfile authorization.txt
http://localhost:8088/AddNumbers/AddNumbersImplService?wsdl
The "authorization.txt" file is an authorization file required for accessing the WSDL. Refer to the following example.
[Example 17.37] << authorization.txt >>
http://jeus:jeus@localhost:8088/AddNumbers/AddNumbersImplService?wsdl
In the previous example, the user name and password are both 'jeus'.
The following settings must be inserted into the client program in order for JAX-WS web service client to authenticate itself.
The following example shows how the aforementioned settings can be inserted into the client program.
Echo port = // … obtaining SEI(Service Endpoint Interface)
((javax.xml.ws.BindingProvider) port).getRequestContext().
put(javax.xml.ws.BindingProvider.USERNAME_PROPERTY, "jeus");
((javax.xml.ws.BindingProvider) port).getRequestContext().
put(javax.xml.ws.BindingProvider.PASSWORD_PROPERTY, "jeus");
String s = port.echoString("JEUS");
At runtime, the JAX-WS web service client engine accesses the remote WSDL to create a dynamic stub, which requires additional authorization. Set the authorization for the client program by using the java.net.Authenticator class.
The following is an example of a client program that uses the java.net.Authenticator class.
[Example 17.38] << AddNumberClient.java >>
public class AddNumbersClient {
...
public void execute() {
Authenticator.setDefault(new MyAuthenticator());
AddNumbersImpl port = new AddNumbersImplService().getAddNumbersImplPort();
((javax.xml.ws.BindingProvider) port).getRequestContext().
put(javax.xml.ws.BindingProvider.USERNAME_PROPERTY, "jeus");
((javax.xml.ws.BindingProvider) port).getRequestContext().
put(javax.xml.ws.BindingProvider.PASSWORD_PROPERTY, "jeus");
int number1 = 10;
int number2 = 20;
port.addNumbers(number1, number2);
...
}
class MyAuthenticator extends Authenticator {
protected PasswordAuthentication getPasswordAuthentication() {
return new PasswordAuthentication("jeus", "jeus".toCharArray());
}
}
}