Table of Contents
This chapter describes advanced settings including dynamic contents and virtual hosting, and how to configure Tmax and JEUS integration.
If the web server is ready, HTML services are available to use. Web browsers can access HTML documents in WebtoB’s Document Root Directory.
This chapter describes the configurations that enable CGI, SSI, and PHP. Also included are examples of configuring dynamic content pages.
In the world wide web, Common Gateway Interface(CGI) is the basic language used to create web pages to communicate information using HTML. Because HTML can only transmit data from the server to the client, it is limited to static, one-dimensional web pages that lack user-server interaction. One method that addresses the weaknesses of HTML is the use of external programs. CGI is the interface used between external programs and web servers.
An external program is called a CGI program or a CGI script. For example, creating a guest book application that can receive comments from visitors is impossible using only HTML. This example and numerous others involving bilateral communication between client and server highlights the need for external programs. C/C++, Perl, UNIX Shell, or Tcl/Tk are common languages used to create CGI programs.
There are many CGI programs that can make a website interactive. A visitor counter, guest book, bulletin board system, web chat rooms, search engine, banners, uploadable file archives, and a form mail system are just a handful of examples of CGI programs.
A well written CGI program is easily transferable to other web servers. WebtoB is one such web server that a CGI program can easily run on.
While there are many ways to create CGI programs, the details will not be discussed in this document. This chapter describes how to configure the use of CGI in WebtoB.
CGI Configuration
In order to use CGI, the following sections must be configured.
-
SVRGROUP section
Add the following content to the SVRGROUP section in order to use CGI. The content is later used in the SERVER section to configure server groups.
The following is an example configuration of the SVRGROUP section. If the SvrType item is set to CGI, the server group processes CGI.
*SVRGROUP cgig NodeName = mynode, SvrType = CGI
-
SERVER section
Specifies the server process in the SERVER section. The following is an example configuration of the SERVER section.
*SERVER cgi SvgName = cgig, MinProc = 10, MaxProc = 10In the example, the server process named cgi is configured. The server group is specified by setting SvgName to cgig. The server process named cgi is now associated with a server group named cgig. Since the SvrType of cgig is CGI, the cgi server provides CGI services.
-
URI section
In the URI section, a specific URI can be mapped to target servers. The following example shows that the URI of "/cgi-bin/" is processed by CGI servers.
*URI uri1 Uri = "/cgi-bin/", SvrType = CGI
-
ALIAS section
In the ALIAS section, the physical directory that processes a URI can be configured to a location other than to Docroot.
The following is an example of ALIAS section configuration.
*ALIAS alias1 Uri = "/cgi-bin/", Realpath = "${WEBTOBDIR}/cgi-bin/"
Note
Refer to "Appendix A. Environment Configuration Example", and "Appendix B. CGI Application Example" for more information on configuration and examples respectively.
This section describes how to use and configure SSI.
SSI Usage
SSI, short for Server Side Includes, can be used to create dynamic web pages. SSI can add Header files or add a function that can automatically adjust the last modified time of a document.
SSI can insert a 'command' in an HTML document. A server parses the SSI document for SSI commands and processes the commands. For example, a SSI command that modifies the last modification time is included in an HTML document; the server parses the command and modifies the last modified time.
Because HTML files that include SSI commands slow performance, SSI is disabled in WebtoB by default. To enable SSI, add a SSI server to the SERVER section in WebtoB environment file so that SSI is processed in another server.
The following is an example of the environment configuration to enable SSI.
*SVRGROUP ssig NodeName = mynode, SvrType = SSI *SERVER ssi SvgName = ssig, MinProc = 10, MaxProc = 10
SSI Commands
All SSI commands in HTML documents are written as HTML comments.
SSI commands are generally wrapped in HTML comments "<!--... -->" as shown in the following. In the example, arg1 and arg2 are parameters and value1 and value2 are their respective values.
<!--#command arg1="value1" arg2="value2" ... -->
The following is an example of flastmod, a command that outputs the modified time. 'file' is a parameter and "nextel.html" is the parameter value.
<!--#flastmod file="nextel.html"-->
SSI command execution is variable name dependent. The following is an example.
<!--#flastmod virtual="/" -->
The echo command retrieves the last modified time of the server web site. When the SSI command is executed, environment variables are set. These variables include CGI variables such as REMOTE_HOST, DOCUMENT_NAME, and LAST_MODIFIED.
<!--#echo var="LAST_MODIFIED" -->
This section describes how to use and configure PHP.
PHP Usage
PHP is a scripting language that is similar to Perl. PHP is popular due to its simplicity and performance advantages. PHP surpasses Perl in performance, development speed, and extendibility. Moreover, PHP is supported in Linux, UNIX, and Win32, which allows for web application development independent of the web server platform.
PHP can do everything that CGI can do such as retrieving form data, creating dynamic web pages, and managing web browser cookies.
PHP Configuration
In order to use PHP in WebtoB, installation is required. Using PHP is similar to using HTML or CGI, making it is easy to apply.
-
SVRGROUP section
A PHP group must be defined in the SVRGROUP and SERVER sections.
In the SVRGROUP section a ScriptLoc item points to the path of the php executable module. The path must be a relative path from ${WEBTOBDIR}. Use the ScriptArgs item to configure the options for PHP executable modules. Files including php.ini must be set to an absolute path.
In the following example, the module path specified in ScriptLoc is "${WEBTOBDIR}/cgi-bin/php" and the ScriptArgs is set to an absolute path.
*SVRGROUP phpg NodeName = mynode, ScriptLoc = "/cgi-bin/php", # refers to "${WEBTOBDIR}/cgi-bin/php" ScriptArgs = "-c /php_conf/php.ini", # executable module options for php execution SvrType = PHP *SERVER php SvgName = phpg, MinProc = 10, MaxProc = 10
If a php3 module is required, additional configuration is necessary. Unlike php4 (.php), php3 uses the ".php3" extension. The use of php3 must be configured in the EXT section. The following is an example of the EXT section configuration.
*EXT
php3 Mimetype = "application/x-httpd-php3",
SvrType = PHP
PHP Example
The following verifies PHP is installed and was configured successfully in WebtoB.
This section describes Virtual Hosts and how to use them.
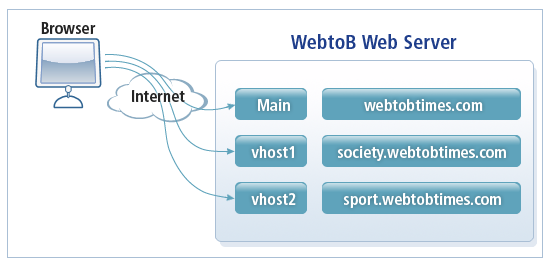
Virtual host is a feature available on web browsers that support HTTP 1.1. Virtual host allows a single web server to work as multiple web servers.
For example, a web newspaper service called “WebtoB Times” is created. This service can operate with a single IP, a domain name, and a single web server. However, multiple domain names can be beneficial so that services can be personalized without having to purchase additional IP addresses. Moreover, multiple domains will allow for easier management of services and future expansion.
The following domain names are offered to customers to specialize services.
-
webtobtimes.com: Main page
-
society.webtobtimes.com: Covers social issues
-
sports.webtobtimes.com: Covers sports issues
Per the previous sample domain names, a virtual host feature can divide domain names to create HTML documents and to provide other services. To support the new domains, the web server can create an independent virtual host for each society and sports domain. The web server can also have separate document paths and configurations for each virtual host. Supporting multiple domains on a single IP address is called Name Based Virtual Host.
Alternatively, there is an IP Address Based Virtual Host that uses multiple domains and multiple IP addresses. However, this is less popular because it is difficult for a server to have multiple IP addresses.
The following is a Virtual Host structure. As shown, a single IP address and a single web server can service multiple domains. The virtual host of WebtoB can also separately process services referred by different names in the same IP.
The following is an example of the WebtoB virtual host configuration of the "WebtoB Times" example from the previous section. For efficient web operation, use VHOST section as follows.
*VHOST
society
Docroot = "society_docs/",
NodeName = webtob,
Hostname = "society.webtobtimes.com",
Port = "8080",
IconDir = "society_icons/",
LOGGING = "society_accesslog",
ERRORLOG = "society_errorlog"
sports
Docroot = "sports_docs/",
NodeName = webtob,
Hostname = "sports.webtobtimes.com",
Port = "8080",
IconDir = "sports_icons",
LOGGING = "sports_accesslog",
ERRORLOG = "sports_errorlog"
When deploying mass virtual hosts, configuring each virtual host is not necessary.
-
Docroot Parameter Configuration
This feature is suitable when the DocRoot parameter is the only parameter modified in the mass virtual hosts. The DocRoot parameter of each virtual host is defined by replacing the server domain name value with the directory configuration pattern.
Docroot = <literal> (Default: "docs/")
E.g., A client connects to http://www.tmax.co.kr. To set the virtual host’s docroot to "${WEBTOBDIR}/docs/www/", configure as follows. Similarly, if a client connects to http://webtob.tmax.co.kr, DocRoot is set to "${WEBTOBDIR}/docs/webtob/".
*VHOST TmaxSoft NodeName = tmax, Hostname = "www.tmax.co.kr" HostAlias = "webtob.tmax.co.kr" Port = "80", Docroot = "${WEBTOBDIR}/docs/%1/"
-
Realpath Parameter Configuration
Specify the Realpath from ALIAS section when using mass virtual hosts. Set the Realpath parameter by replacing the server domain name value with the directory configuration pattern.
Realpath = <literal> (Default: mandatory)
Similar to configuring DocRoot, "%1" is replaced with the first field of the domain requested by the client.
*ALIAS alias1 Uri = "/cgi-bin", Realpath = "${WEBTOBDIR}/docs/%1/cgi-bin/"
When using mass virtual hosts, the directory configuration pattern can be configured dynamically by using the following directives.
| Directive | Description |
|---|---|
| %p | Changes into the requested port number. |
| %n | Changes into the Hostname or the Nth element of the IP address. If n is set to 0, the entire string is used. If the value starts with a minus symbol (-), count from the end of the Hostname or IP address. If a plus symbol (+) follows, the rest of the Hostname or IP address is used. |
| %n.m | Changes into the Mth character of the Nth element. Minus (-) or plus (+) symbols can be used as previously described. |
| %% | Change into a single percent symbol (%). |
Note
When a %-directive is used, an absolute path must be configured for Docroot/Realpath. When an environment variable ${env} is used, a %-directive can be only used when the changed path is an absolute path.
This section describes log files and their formats.
WebtoB stores all logs related to web service requests and services it provides into a log file specified in the environment file. The log file can be analyzed for various client and request data.
The log file, stored in the location specified in the environment file, can be stored anywhere in the machine. Improper log maintenance may cause performance and capacity issues for the server.
-
System burden is generated when an event is recorded to the log. Although the logging mechanism within WebtoB is efficient, physical limitations, such as disk speed, may hinder system performance.
-
While system burden is insignificant for few clients, a large scale website can generate gigabytes worth of logs daily. Logs are not recorded if there is insufficient disk capacity, thus requiring maintenance.
Log data is critical to system administrators. Web services can become more effective by mining user information. E.g., An online shopping mall administrator can obtain customer information to help increase sales. Because of the importance of logs, WebtoB administrators store log files to a specified location for management.
WebtoB creates three types of logs: an access log that is related to user requests; an error log that is related to error messages generated during processing requests; and a system log for the WebtoB system.
WebtoB can save access logs in multiple formats by configuring the Format item in the LOGGING section.
CLF (Common Logfile Format) is a standardized text format used by many administrators. Because the format is standardized and originated from NCSA, most web servers support this format. In WebtoB, CLF is the default log format.
The Common Logfile Format defined in W3C is as follows.
remotehost rfc931 authuser [date] "request" status bytes
Define log parameters in the following order. Store the log in the location specified in the WebtoB environment file.
| Item | Description |
|---|---|
| remotehost | Remote hostname. (If the DNS hostname is unavailable or DNSLookup is off, enter an IP address.) Refer to https://www.w3.org/Daemon/User/Config/General.html#DNSLookup for more information on Remote Host. |
| rfc931 | Name of remote log |
| authuser | Name of authorized user |
| [date] | Date and time of the request |
| "request" | The request line exactly as it came from the client |
| status | HTTP Status Code returned to the client Refer to http://www.w3.org/Protocols for more information on Status Codes. |
| bytes | Size of transmitted document |
The following is an example of the log files stored in WebtoB.
143.248.148.42 - - [13/Feb/2001:16:46:13 +0900] "GET / HTTP/1.1" 304 - 143.248.148.42 - - [13/Feb/2001:16:46:14 +0900] "GET /index_pb.gif HTTP/1.1" 304 - 143.248.148.42 - - [13/Feb/2001:16:46:18 +0900] "GET /index.html HTTP/1.1" 200 7118 143.248.148.42 - - [13/Feb/2001:16:46:18 +0900] "GET /usage.png HTTP/1.1" 304 - 143.248.148.42 - - [13/Feb/2001:16:46:37 +0900] "GET /usage_200102.html HTTP/1.1" 404 148 143.248.148.42 - - [13/Feb/2001:16:47:21 +0900] "GET /index.html HTTP/1.1" 304 - 143.248.148.42 - - [13/Feb/2001:16:47:21 +0900] "GET /usage.png HTTP/1.1" 200 2509 143.248.148.42 - - [13/Feb/2001:16:47:24 +0900] "GET /usage_200102.html HTTP/1.1" 404 148 143.248.148.42 - - [13/Feb/2001:16:47:55 +0900] "GET /index.html HTTP/1.1" 304 - 143.248.148.42 - - [13/Feb/2001:16:47:55 +0900] "GET /usage.png HTTP/1.1" 304 - 143.248.148.42 - - [13/Feb/2001:16:47:57 +0900] "GET /usage_200102.html HTTP/1.1" 200 30798
In the example, a "-" in a field indicates missing data. The first column in the example displays the IP address of the connected client. In the following hyphens (-) represent the missing rfc931 and AuthUser data. In the square bracket [ ], user access time is displayed.
The information wrapped in double quotes is the request line from the client. The xnxt column is the HTTP status code of the response to the client. The last column is size of the object transmitted to the client from the server in bytes.
In WebtoB, the log format is configured in the Format item of the LOGGING section.
In order to record logs, configure the environment as follows:
*NODE
webmain
WebtoBDir = "$WEBTOBDIR",
SHMKEY = 69000,
DOCROOT = "docs/",
Port = "5469",
Logging = "accesslog",
ErrorLog = "errorlog"
*LOGGING
accesslog
Format = "default",
Filename = "log/access.log",
Option = "Sync"
errorlog
Format = "",
Filename = "log/error.log",
Option = "Sync"
The Logging item in the NODE section specifies the access log, while the ErrorLog item specifies the error log. In the LOGGING section of the configuration, the accesslog and errorlog sections define the log format, filename, and options of their respective logs.
The following directives can be used in format items to customize access logs.
| Format | Description |
|---|---|
| DEFAULT | Default log file format. (Format string: "%h %t \"%r\" %s %b %D") |
| COMMON | Common log file format. (Format string: "%h %l %u %t \"%r\" %s %b") |
| COMBINED | Combined log file format. (Format string: "%h %l %u %t \"%r\" %s %b \"%{Referer}i\" \"%{User-Agent}i\") |
| %a | Displays the IP address of the machine that sent the request. Same as %h. |
| %b | Displays the byte of the response object. |
| %c | Displays whether the response is in the WebtoB internal cache (specified as "hc"). |
| %{_attr_name_}C | Displays '_attr_name_' value of the HTTP Request Cookie Header. |
| %d | Displays the time a response was sent. |
| %D | Displays the time spent processing the request. (unit: millisecond) |
| %{ENV_NAME}e | Displays the environment variable ENV_NAME. |
| %g | Displays the request identifier used internally by WebtoB. |
| %h | Displays the IP address of the machine that sent the request. Same as %a. |
| %H | Displays the HTTP version used. |
| %{HEADER_FIELD}i | Displays the HEADER_FIELD Header value of the HTTP request. |
| %{_id_name_}J | Displays the ID that is used internally when a request is forwarded to JEUS for processing.
|
| %m | Displays the HTTP request method. |
| %p | Displays the server port that received the request. |
| %q | Displays the query value of HTTP request. |
| "%r" | Displays the entire request line of the HTTP request. |
| %R | Displays all request lines of the HTTP request. Displays request lines that are changed by CheckURL or URLRewrite function. |
| %s | Displays the HTTP Status Code used in the response. |
| %t | Displays the time when the request processing completed. |
| %T | Displays the time spent processing the request. (unit: second) |
| %u | Displays the user name used in HTTP authentication. |
| %U | Displays the HTTP Request URI. |
| %v | Displays the Host Header field value. |
| %z | If the response is compressed, displays the response size and compression rate before and after the compression. |
"%h %l %u %t \"%r\" %s %b" corresponding to CLF, is set as the default value. In the previous example, the accesslog was set to default CLF format.
Including the %d option, several date and time types provided by the strftime function can be specified within {}. The default value is recorded in the same format as the %t directive: "[13/Feb/2001:16:47:24 +0900]".
The following format can be specified using directives.
custom_log1
Format = "%h %l %u %t \"%r\" %s %b",
Filename = "log/custom1.log"
custom_log2
Format = "[%{%Y.%m.%d %H:%M:%S}d] %a \"%r\" %s %T",
Filename = "log/custom2.log"
WebtoB utilizes the ASP library to integrate with TmaxSoft TP-Monitor Tmax. Tmax must be installed before integration.
In WebtoB, only a client program can be created using WBAPI, while server programs are used in Tmax. I.e., the WebtoB client program sends a request to the server program in Tmax. After the client program receives a response, the response is transferred to the WebtoB client (web browser).
Because integration with Tmax uses WBAPI, creating an environment file is the same. The following example is an environment file.
<apsl.m>
*DOMAIN
webtob_apsl
*NODE
tmaxi2
WebtoBDir="$WEBTOBDIR",
SHMKEY = 74125,
Docroot = "docs/",
Port = "8797",
HTH = 1,
Logging = "log1",
AppDir = "ap/",
ErrorLog = "log2"
*SVRGROUP
htmlg NodeName = "tmaxi2", SvrType = HTML
webapg NodeName = "tmaxi2", SvrType = WEBSTD
*SERVER
wbsvrinit SvgName = webapg, MinProc = 10, MaxProc = 10
wbquery SvgName = webapg, MinProc = 10, MaxProc = 10
wbsession SvgName = webapg, MinProc = 10, MaxProc = 10
*SERVICE
test SvrName = wbsvrinit
query SvrName = wbquery
wbsession SvrName = wbsession
*URI
uri1 Uri = "/svct/", SvrType = WEBSTD
*LOGGING
log1
Format = "default",
Filename = "log/access.log",
Option="Sync"
log2
Format = "",
Filename = "log/error.log",
Option="Sync"
Refer to "Appendix C. Integration with Tmax" for more information on the apsl.m client program from the previous example.
WebtoB can integrate with JEUS, TmaxSoft's next generation web application server, which includes advanced features not available on web servers. JEUS, well suited for large data transactions and user management, can help E-commerce web sites to ensure security and transactions to clients.
The integration procedures for WebtoB Standard and JEUS are nearly identical to the integration procedures for WebtoB Enterprise and its servlet engine.
The following files must be configured in order to integrate WebtoB with JEUS.
-
WebtoB environment file (e.g., http.m)
-
JEUS environment file: WEBMain.xml
The following values must be identical in the WebtoB and JEUS configurations.
-
WebtoB-JEUS communication port number
-
Number of HTH
-
Server Name (WebtoB's JSV Server Name and JEUS’s Registration ID)
-
Number of Processes (WebtoB’s MinProc/MaxProc and JEUS’s Thread-pool)
In WebtoB and JEUS integration, JEUS connects to WebtoB. For best results, WebtoB should service the external network and JEUS the internal network. This is because internal network firewall is very strict with in-bound connections but tolerant with outbound connections.
When connecting JEUS to WebtoB, it is recommended to first start WebtoB and then JEUS. JEUS will attempt to connect to WebtoB during start up. If WebtoB is not online, JEUS will continually try to connect to WebtoB at regular intervals and output error messages to the JEUS log. Once the a successful connection has been made, a connection confirmation message is outputted to the JEUS log. With the successful connection, user requests, such as Servlet and JSP, are sent to JEUS through the connection.
The WebtoB and JEUS connection is persistent and does not disconnect unless a network error or a server failure occurs.
WebtoB Servlet Engine is sufficient for a business that requires simple online business services and logic. However, if a large-scale online service system is required, an integrated WebtoB and JEUS system is recommended.
Note
This section describes integration with JEUS version 6 and higher. For the information about JEUS 7 integration, refer to "4.5.3. Using Embedded Servlet Engine (Enterprise)".
WebtoB Environment File Configuration
-
NODE Section
Specifies the number of HTH processes and the JsvPort that communicates with JEUS.
*NODE … HTH = 1, JsvPort = 9999, …The number of HTH processes specified must be the same as the <hth-count> item value, which is a subitem of <webtob-listener> in the JEUS environment file WEBMain.xml.
JsvPort is a port number that connects to a web container. The web container is unrelated to port numbers that receive requests as an actual web browser. This port must be same as the <port> item value, which is a subitem of <webtob-listener> in WEBMain.xml.
-
SVRGROUP Section
Specifies a new server group with a SVRTYPE of JSV.
*SVRGROUP jsvg SvrType = JSV -
SERVER Section
By connecting a service to a web container, specifies the server.
*SERVER MyGroup SvgName = jsvg, MinProc = 4, MaxProc = 10The server named MyGroup is associated with the server group jsvg, which is defined in the SVRGROUP section.
MinProc is the minimum number of connections to the web container. MaxProc is the maximum number of connections allowed to the web container. MinProc and MaxProc need to be greater than or equal to the value in <thread-pool>, which is a subitem of <webtob-listener> in WEBMain.xml.
-
URI Section
URI is the identifier WebtoB uses to decide which server to use. In the URI section, the server name (MyGroup), server type (JSV), and the URI to be serviced are specified.
The following is an example configuration that performs a service on the JSV server (MyGroup) for URI "/examples/".
*URI uri1 Uri = "/examples/", SvrType = JSV, SvrName = MyGroup
JEUS 6 Environment File Configuration
The following path found in WEBMain.xml must be modified for the WebtoB connection configuration.
$JEUS_HOME/config/<node_name>/<node_name>_servlet_<engine_name>/
<WEBMain.xml>
<webtob-listener>
<listener-id>webtob1</listener-id>
<port>9999</port>
<webtob-address>localhost</webtob-address>
<registration-id>MyGroup</registration-id>
<hth-count>1</hth-count>
<thread-pool>
<min>10</min>
<max>10</max>
<step>0</step>
<max-idle-time>30000</max-idle-time>
</thread-pool>
</webtob-listener>
In WEBMain.xml, the items under <webtob-listener>, which is under <webserver-connection>, must be modified. The following are descriptions for each item.
| Tag | Description |
|---|---|
| <port> | The port used to communicate between WebtoB Servlet Engine Web Container and WebtoB. The specified port value must be the same as the JsvPort value in the NODE section of the WebtoB configuration file. |
| <webtob-address> | Specifies the IP address that connects to WebtoB. |
| <registration-id> | Used when the first connection to WebtoB is made. <registration-id> must be the same as the server name specified under the SERVER section (E.g., MyGroup). |
| <hth-count> | Set as the same value as HTH of the NODE section of WebtoB. An actual connection is made for each HTH, therefore this value must match the number of HTH. |
| <thread-pool>, <min>,<max> | The minimum and maximum number of threads of Thread Pool. The value should be smaller than or equal to the value of MinProc/MaxProc for the MyGroup server defined in the WebtoB environment file. |
A context group can be connected to many web servers. Each web server must have a communication port. Being connected to many web servers is useful when multiple web servers are in different nodes or when receiving requests from multiple types of web servers.
Servlet Engine Starting Up And Shutting Down
WebtoB and WebtoB Servlet Engine can be started by using the steps listed in the following into a command console.
-
Compile the WebtoB environment file.
C:\> wscfl –i http.m
-
Start WebtoB.
C:\>wsboot
-
Start JEUS Manager.
C:\>jeus
-
In order to boot JEUS, use the jeusadmin console tool after authentication.
C:\>jeusadmin webmain Login name>administrator Password> JEUS 6.0 Jeus Manager Controller webmain>
webmain is the node that boots JEUS. Authorized user name and password are required to use the jeusadmin command.
Note
Default ID is administrator and the default password is the password entered at JEUS installation.
-
Boot JEUS, which automatically integrates with WebtoB.
webmain> boot
The booting process is a two-step procedure.
-
Start JEUS service and then its engine.
-
During the JEUS server start-up process, the previous command is passed to JEUS Manager.
-
-
Stop JEUS service and its engine using the following command.
webmain> down
-
Exit JEUS server using the following command.
webmain>jeusexit
Example
Refer to "A.2. WebtoB and JEUS Integration Configuration" for more information.
The servlet engine provided by WebtoB Enterprise or above can be configured in the same way as when integrating JEUS. However, the aforementioned item names for JEUS 6 may be different from the current Servlet Engine version, which is for JEUS 7.
WebtoB Environment File Configuration
Configuration is identical to "WebtoB environment file configuration" in "4.5.2. JEUS 6 Integration Configuration (Standard+)".
Embedded Servlet Engine Environment File Configuration
For WebtoB connection configuration, domain.xml in the following path must be modified.
${WEBTOBDIR}/jeus/domains/domain1/config/domain.xml
<domain.xml>
<webtob-connector>
<name>webtob</name>
<network-address>
<port>9999</port>
<ip-address>localhost</ip-address>
</network-address>
<hth-count>1</hth-count>
<thread-pool>
<number>10</number>
</thread-pool>
<registration-id>MyGroup</registration-id>
<output-buffer-size>8192</output-buffer-size>
<reconnect-interval>5000</reconnect-interval>
</webtob-connector>
Items in the <webtob-connector> section must be modified in domain.xml. Descriptions for each item are as follows:
Starting and Terminating an Embedded Servlet Engine
In the commandline mode, start WebtoB and its embedded servlet engine in steps. For information about configuration, refer to the JEUS7 fix#4 manual.
-
Compile the WebtoB environment file.
C:\> wscfl –i http.m
-
Start WebtoB.
C:\>wsboot
-
Use the following command to start JEUS DAS.
C:\>startDomainAdminServer -u administrator -p <password>
-
Use the following command to start JEUS MS.
C:\>startManagedServer -domain jeus_domain -server server1 -u administrator -p <password>
Once JEUS MS boots up successfully, open "http://localhost:8088/examples/" in the web browser to check that "examples" has been properly deployed.
-
Use the following command to connect to jeusadmin.
C:\>jeusadmin -u administrator -p <password> Attempting to connect to 127.0.0.1:9736. The connection has been established to Domain Administration Server adminServer in the domain jeus_domain. JEUS7 Administration Tool To view help, use the 'help' command. [DAS]jeus_domain.adminServer>
Enter the JEUS Admin user name and password. The default user name is 'administrator' and the password is the one that was entered when installing the Servlet Engine.
Once JEUS starts successfully, a prompt will be displayed and is ready for command input.
-
Use the WebAdmin to manage the Servlet Engine.
http://localhost:9736/webadmin
Go to the previous URL from the web browser.
Enter the JEUS Admin user name and password, and then click [Login]. The default user name is 'administrator' and the password is the one that was entered when installing JEUS.
-
Use the following command to terminate JEUS service and engine.
[DAS]jeus_domain.adminServer>local-shutdown
-
Use the following command to terminate jeusadmin.
exit
Example
Refer to "A.2. WebtoB and JEUS Integration Configuration" for more information.
WebtoB can connect to another web application server besides JEUS using Reverse Proxy. A web application server generally has an HTTP Listener, and WebtoB uses reverse proxy setting to connect with another web application server's HTTP Listener.
Multiple web application servers can be configured using the Reverse Proxy Group setting provided in WebtoB Enterprise edition or higher.
WebtoB and web application server connection can be configured in the following files.
-
WebtoB environment file (e.g., http.m)
-
WAS environment file (e.g., WEBMain.xml)
Check the following items for WebtoB-web application server connection. (Refer to the target web application server's manual for its configuration.)
-
Target server's HTTP Listener setting (Listen IP, Port, thread count).
-
Application setting for PING check when using persistent connection.
-
Routing ID when using Sticky Session routing.
-
HTTP Listener's SSL setting when using encrypted communication.
WebtoB uses the Reverse Proxy setting to connect to another web application server. The setting can also be used when WebtoB runs in an external network while the web application server runs in an internal network. In this setting, WebtoB can rewrite a response received from the internal server.
WebtoB attempts to connect to the target server when a client initiates an HTTP request. If the server is not running, it returns a 503 error to the client. If the connection is successful, WebtoB forwards the request to the server, receives a response from the server, and then sends it to the client.
WebtoB can reuse the connection by using the persistent connection setting, and this requires the PING check setting between the two servers. If the Min and Max settings are configured, connection is managed according to the number of concurrent requests and SSL communication can be used.
The WebtoB Enterprise edition provides the Reverse Proxy Group setting for a multi web application server configuration, and the Reverse Proxy setting can be used when connecting to a single server.
WebtoB Environment File Configuration
-
REVERSE_PROXY_GROUP Section
Configure the following to create a Reverse Proxy Group.
*REVERSE_PROXY_GROUP rproxyG1 VhostName = "vhost1", PathPrefix = "/before/", RegExp = "\.(do|jsp)$", ServerPathPrefix = "/after/", RewriteHtmlUrl = "/after/ /before/", HtmlUrl = "a href", HtmlUrl = "img src", HtmlUrl = "link href", HtmlUrl = "script src", HtmlUrl = "frame src", HtmlUrl = "td background", HtmlUrl = "table background", HtmlUrl = "iframe src", HtmlUrl = "OBJECT CODEBASE", RewriteHtmlMaxSize = 4194304, WBRoutingCookieKey = "W2BRID" #SessionIDCookieKey = "JSESSIONID"The previous setting changes the prefix of the requested service from "/before/" to "/after/".
Since each server provides the same service in a multi web application server configuration, the VhostName, PathPrefix, RegExp, and ServerPathPrefix items in the Reverse Proxy Group and Reverse Proxy must be set identically or set only in the Reverse Proxy Group.
To use a routingid separate from the server's Sticky Session routingid, use the WBRoutingCookieKey setting.
-
REVERSE_PROXY Section
Configure the Reverse Proxy Group name, the target server's HTTP Listener information (Ip:Port), and each server's connection information.
*REVERSE_PROXY rproxy1 ServerAddress = "127.0.0.1:8088", ReverseProxyGroupName = "rproxyG1", MinPersistentServerConnections = 1, MaxPersistentServerConnections = 20, PersistentServerCheckTime = 50, PersistentServerTimeout = 300, PersistentServerCheckUrl = "/after/ping.html", MaxWebSocketConnections = 20 #StickySessionRoutingID = "was1_servlet_engine", #ProxySSLFlag = Y, #ProxySSLName = pssl1 rproxy2 ServerAddress = "127.0.0.1:8089", ReverseProxyGroupName = "rproxyG1", MinPersistentServerConnections = 1, MaxPersistentServerConnections = 20, PersistentServerCheckTime = 50, PersistentServerTimeout = 300, PersistentServerCheckUrl = "/after/ping.html", MaxWebSocketConnections = 20 #StickySessionRoutingID = "was2_servlet_engine", #ProxySSLFlag = Y, #ProxySSLName = pssl1In the previous settings, rproxy1(127.0.0.1:8088) and rproxy2(127.0.0.1:8089) are set in the rproxyG1, and requests are routed in RR(Round Robin) fashion. If there are multiple connections in a single Reverse Proxy, connections are assigned to each request in FA (First Assign) manner.
MaxPersistentServerConnections specifies the maximum number of concurrent requests that can be processed. When the number of requests exceeds this limit, any additional requests are queued.
MinPersistentServerConnections specifies the minimum number of connections that must be maintained even if there are no requests. Connections in excess of this count are disconnected after the PersistentServerTimeout period .
PersistentServerCheckTime specifies the interval for sending a ping message to maintain the connection with the target server, and it must be set to a value less than the KeepAliveTimeout setting of the target server's HTTP Listener. Otherwise, the server will terminate the connection first. WebtoB maintains the connection by sending a ping at the specified interval and receiving a response from the server. This way, WebtoB can configure a connection pool of connections with other servers and dynamically maintain each connection.
A ping message is an HTTP HEAD request created with the PersistentServerCheckUrl setting. The ping message in the previous example is "HEAD /after/ping.html HTTP/1.1". Since the HEAD method only gets the HTTP Response Header, it minimizes the size of the response (pong) to a ping message. The target server must create the "/after/ping.html" application in order to respond to a ping.
When using the WebSocket for the connection, then number of WebSocket connections can be limited by using the MaxWebSocketConnections.
If the WBRoutingCookieKey is set for the Reverse Proxy Group, self-routing is used for rproxy1 and rproxy2. For a response that is processing through rproxy1, the WBRoutingCookieKey and rproxy1 are encoded in Base64 and added to the Set-Cookie header. Any subsequent requests from the same client are routed to rproxy1 by using the encoded value in the cookie. If WBRoutingCookieKey is not used, the StickySessionRoutingID is used with the Reverse Proxy Group's SessionIDCookieKey setting for Sticky Session routing. This requires that the target server add the engine name after the dot(.) character of the JSESSIONID value in the "Set-Cookie" Response Header.
ProxySSLFlag and ProxySSLName are specified for using SSL encryption communication between WebtoB and the target server.
-
PROXY_SSL Section
Configure the SSL encryption communication setting between WebtoB and the target web application server.
*PROXY_SSL pssl1 Verify = 2, VerifyDepth = 1, RequiredCiphers = "ALL:!ADH:!EXPORT56:RC4+RSA:!SHA:+HIGH: +MEDIUM:+LOW:+SSLv2:+EXP:+eNULL", CACertificateFile="$(WEBTOBDIR)/ssl/server.crt", CheckPeerValidPeriod = YSince WebtoB acts as the client and the target server as the server in this case, the target server must be configured with SSL encryption. If configured, WebtoB connects to the target server via TCP, and then requests for an SSL Handshake.
To verify the certificate during the SSL Handshake protocol, set the Verify item to 2 and set it to 0 otherwise. The CACertificateFile setting must be configured to verify the server certificate.
Checking the Configuration, Statistics, and Connection State
Use the wsadmin to check the configuration, statistics, and state of each connection.
-
Checking the Reverse Proxy Group settings.
wsadmin> cfg -rpg REVERSE_PROXY_GROPUP(0): Name = rproxyG1, VhostName = "vhost1", PathPrefix = "/before/", ServerPathPrefix = "/after/", RewriteHtmlMaxSize = 4194304, RewriteHtmlUrl = "/after/ /before/", HtmlUrl = "a href", HtmlUrl = "img src", HtmlUrl = "link href", HtmlUrl = "script src", HtmlUrl = "frame src", HtmlUrl = "td background", HtmlUrl = "table background", HtmlUrl = "iframe src", HtmlUrl = "OBJECT CODEBASE", SessionIdCookieKey = "JSESSIONID", FlexibleStickySessionRouting = N # (N:0, Y:1), ReverseProxyEntries = 2 -
Checking the Reverse Proxy settings
wsadmin> cfg -rp REVERSE_PROXY(0): Name = rproxy1, ReverseProxyGroupName = "rproxyG1", VhostName = "vhost1", PathPrefix = "/before/", ServerPathPrefix = "/after/", ServerAddress = "127.0.0.1:8088", HttpInBufSize = 16384, RewriteHtmlMaxSize = 4194304, RewriteHtmlUrl = "/after/ /before/", HtmlUrl = "a href", HtmlUrl = "img src", HtmlUrl = "link href", HtmlUrl = "script src", HtmlUrl = "frame src", HtmlUrl = "td background", HtmlUrl = "table background", HtmlUrl = "iframe src", HtmlUrl = "OBJECT CODEBASE", MinPersistentServerConnections = 1, MaxPersistentServerConnections = 20, PersistentServerCheckTime = 50, PersistentServerTimeout = 300, PersistentServerCheckUrl = "/after/ping.html", ProxySslFlag = N REVERSE_PROXY(1): Name = rproxy2, ReverseProxyGroupName = "rproxyG1", VhostName = "vhost1", PathPrefix = "/before/", ServerPathPrefix = "/after/", ServerAddress = "127.0.0.1:8089", HttpInBufSize = 16384, RewriteHtmlMaxSize = 4194304, RewriteHtmlUrl = "/after/ /before/", HtmlUrl = "a href", HtmlUrl = "img src", HtmlUrl = "link href", HtmlUrl = "script src", HtmlUrl = "frame src", HtmlUrl = "td background", HtmlUrl = "table background", HtmlUrl = "iframe src", HtmlUrl = "OBJECT CODEBASE", MinPersistentServerConnections = 1, MaxPersistentServerConnections = 20, PersistentServerCheckTime = 50, PersistentServerTimeout = 300, PersistentServerCheckUrl = "/after/ping.html", ProxySslFlag = N -
Checking the Reverse Proxy SSL settings.
wsadmin> cfg -pssl PROXY_SSL(0): Name = pssl1, Verify= 2, VerifyDepth = 1, CheckPeerValidPeriod = Y # (N:0, Y:1), CACertificatePath = "/home/tmax/server/webtob/ssl/", CACertificateFile = "/home/tmax/server/webtob/ssl/server.crt", Protocols = "SSLv2, SSLv3, TLSv1, TLSv1.1, TLSv1.2", RequiredCiphers = "ALL:!ADH:!EXPORT56:RC4+RSA:!SHA:+HIGH: +MEDIUM:+LOW:+SSLv2:+EXP:+eNULL" -
Checking the statistics and connection information of the Reverse Proxy Group.
wsadmin> st -rpg -------------------------------------------------------------------------------- hth (rpgi)rpgname rproxyname count(qcnt) avg cons remote_ipaddr:port -------------------------------------------------------------------------------- 0 ( 0)rproxyG1 rproxy1 1( 0) 0.0025 1 127.0.0.1:8088 0 ( 0)rproxyG1 rproxy2 1( 0) 0.0021 1 127.0.0.1:8089
The following describes each column of the output.
Column Description count Total processed requests qcnt Number of queued requests for the Reverse Proxy Group (qcnt for rproxy1 and rproxy2 would be the same) avg Avg. processing time (sec) cons Number of connections to the target server -
Checking the statistics and connection information of each Reverse Proxy
wsadmin> st -rp HTH 0: RDY ------------------------------------------------------------------------------ (rpi)rproxy_name rpgname status count idle spri clid ssl websocket ------------------------------------------------------------------------------ ( 0)rproxy1 rproxyG1 RDY 1 14 1 -1 N N ( 1)rproxy2 rproxyG1 RDY 1 10 2 -1 N N
The following describes each column of the output.
Column Description status Connection state count Total processed requests idle Idle time (sec) spri Internal connection index clid Client index of the currently processing request ssl Option to use SSL websocket Whether websocket connection is used
Apache's mod_rewrite function has been ported to WebtoB. This function provides a rule-based URL rewriting function.
In order to use the URLRewrite function, the URLRewrite item in the NODE section must be set to "Y". In the URLRewriteConfig item, configuration related to Condition and Rule must be set.
The following is an example of the NODE section configuration needed to use the URLRewrite function.
*NODE
mynode
URLRewrite = Y,
URLRewriteConfig = "${WEBTOBDIR}/config/rewrite.conf"
In URLRewriteConfig, RewriteCond and RewriteRule configurations can be used among the mod_rewrite functions of Apache. However, all configurations are not available, and some functions that will be later described are unavailable.
Note
The following description of the URLRewriteConfig configuration was written in reference to "Apache 2.2 mod_rewrite". Some functions may not be supported in WebtoB.
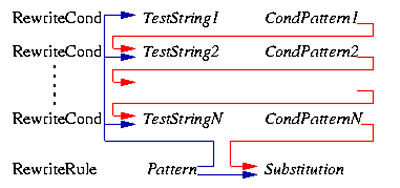
In order to configure RewriteCond, specify rewriting conditions as follows. Compare the TestString and Condpattern. If the conditions are met, RewriteCond is changed to the pattern defined in RewriteRule configuration.
RewriteCond <TestString> <CondPattern> [flags]
-
<TestString>
In TestString, the following reserved words and general strings can be used.
-
$N (0 <= N <= 9)
-
Refer to the pattern wrapped in parentheses among RewriteRule's patterns.
-
-
%N (1 <= N <= 9)
-
Refer to the pattern wrapped in parentheses among RewriteCond's CondPatterns.
-
-
%{SERVER_VARIABLE_NAME}
Refer to the additional variables among the server environment variables used in CGI.
-
%{ENV:variable} refers to the environment variable.
-
%{HTTP:header} refers to HTTP Request Header.
-
The following variables can also be used.
Variable Description HTTP headers HTTP_USER_AGENT, HTTP_REFERER, HTTP_COOKIE, HTTP_FORWARDED, HTTP_HOST, HTTP_PROXY_CONNECTION, HTTP_ACCEPT connection & request REMOTE_ADDR, REMOTE_PORT, REMOTE_USER, REMOTE_METHOD, QUERY_STRING, AUTH_TYPE
server internals DOCUMENT_ROOT, SERVER_NAME, SERVER_ADDR, SERVER_PORT, SERVER_PROTOCOL, SERVER_SOFTWARE date and time TIME_YEAR, TIME_MON, TIME_DAY, TIME_HOUR, TIME_SEC, TIME_WDAY, TIME specials THE_REQUEST, REQUEST_URI, HTTPS Note
%{SSL:variable}, %{LA-U:variable}, %{LA-F:variable}, REMOTE_HOST, REMOTE_IDENT, SCRIPT_FILENAME, SCRIPT_USER, SCRIPT_GROUP, SERVER_ADMIN, API_VERSION, REQUEST_FILENAME, IS_SUBREQ variables provided from Apache mod_rewrite cannot be used.
-
-
-
<CondPattern>
CondPattern can use Perl compatible regular expressions. The following additional patterns can also be used.
Directive Description !Pattern Specifies the cases that do not match the specified pattern(s). <CondPattern Matches when TestString is before CondPattern alphabetically. >CondPattern Matches when TestString is after CondPattern alphabetically. =CondPattern Matches when TestString is same as CondPattern. -d Matches when TestString is considered a path and it is a directory. -f Matches when TestString is considered a path and it is a file. -s Matches when TestString is considered a path and the file size is greater than 0. -l Matches when TestString is considered a path and it is a symbolic link. -x Matches when TestString is considered a path and it is an executable file. -F Matches when TestString is considered a path and it is accessible in server configuration. -U Matches when TestString is considered a URL and it is accessible in server configuration. Note
All of these patterns can be prefixed by an exclamation mark '!' to negate their meaning.
The following are descriptions for Regex vocabulary.
Directive Description . Matches any single character. + Repeats the previous match one or more times. * Repeats the previous match zero or more times. ? Makes the match optional. ^ Matches the beginning of the string. $ Matches the end of the string. ( ) Groups several characters into a single unit and captures a match to use in a back reference. [ ] A character class - matches one of the characters. [^ ] A negative character class - matches any character not specified.
-
[flags]
The pattern matching method can be modified by using [flag]s in the CondPattern.
Directive Description nocase|NC Not case-sensitive in pattern matching. ornext|OR If a different RewriteCond exists after RewriteCond, combine the next RewriteCond with the logical OR operator. If not explicitly specified, the next condition is combined with AND. novary|NV If HTTP Header is used as TestString, do not add Vary Header to Response. The following is an example of using the [OR] flag.
RewriteCond %{HTTP_HOST} ^host1.* [OR] RewriteCond %{HTTP_HOST} ^host2.* [OR] RewriteCond %{HTTP_HOST} ^host3.* RewriteRule ...If the [OR] flag is not used, each RewriteCond/RewriteRule must be written separately.
RewriteRule configures the rewriting of user requests. If a user request is matched to a RewriteCond, the matched pattern in the user request is replaced by a substitution specified in the RewriteRule configuration.
RewriteRule <Pattern> <Substitution> [flags]
-
-
Patterns can use Perl compatible regular expressions. If '!' (not) is used, the cases where patterns do not match, can be specified.
Note
If '!' is used, the group pattern ($N) wrapped in parentheses cannot be used because the cases are for unmatched patterns do not have values for group patterns ($N).
-
If RewriteRule is used alone, pattern matching uses URL-path. If RewriteRule is used with RewriteCond, the final matched pattern is used.
-
-
Specifies what to substitute the matched URL with. The following values can be used.
Value Description file-system path When specifying the absolute path of the file system that starts with '/', use the file in the user response. However, the configured path must exist in the file-system. URL-path When a general URL path is used, use the appropriate resource. Absolute URL If an absolute URL is specified (E.g., "http://<hostname>/file.html"), mod_rewrite checks to see whether the hostname matches the current host. If the hostname matches, the scheme and hostname are stripped out and the resulting path is treated as a URL path. Otherwise, an external redirect is performed for the given URL. - '-' means no substitution should be performed. $N (N=0..9) Indicates the Nth group pattern among RewriteRule's patterns. %N (N=1..9) Indicates the Nth group pattern among the last matched RewriteCond patterns. %{VARNAME} Refers to VARNAME provided by the server. The items applied to TestString of RewriteCond can be used. ? The Query string is not changed. In order to change the string, add '?' to the substitute string. In order to delete a query string, place a '?' at the end of the substitute string.
Note
WebtoB does not support RewriteMap provided by mode_rewrite in Apache. ${mapname:key|default} cannot be used.
-
-
Special actions of RewriteRule can be configured with [flag]s.
-
Multiple flags can be used by separating each flag with a comma (,). The following values can be used.
-
B (escape back references)
The [B] flag turns the '%' escape encoding off. During substitution of the URL string, the '%' character is read as just a regular character and not as a special escape character.
For example, in "/C%2b%2b" the '%' character triggers an escape and the string is mapped to "index.php?show=/C++". However, if the [B] option is used, the URL is mapped to "index.php?show=/C%2b%2b".
RewriteRule ^(.*)$ index.php?show=$1
-
chain|C (chained with next rule)
If this option is set, when a rule is not matched, the next rule will not be checked. If the next rule uses the [C] option, it is also skipped.
-
cookie|CO=NAME:VAL:domain[:lifetime[:path[:secure[:httponly]]]] (set cookie)
Add the Set-Cookie Header to a response to add a Cookie to a user's browser.
-
discardpathinfo|DPI (discard PATH_INFO)
In per-directory context, RewriteRule distinguishes URI and PATH_INFO and combines URI and PATH_INFO each time the rule is applied.
[DPI] options apply RewriteRule without distinguishing PATH_INFO.
-
env|E=VAR:VAL (set environment variable)
Adds VAR=VAL to an environment variable. In VAL, regexp backreferences ($N or %N) can be used. This environment variable can be used in SSI or CGI and can be used as %{ENV:VAR} among RewriteCond patterns.
-
forbidden|F (force URL to be forbidden)
Responds as "403 Forbidden".
-
gone|G (force URL to be gone)
Responds as "410 Gone".
-
handle|H=Content-handler (force Content handler)
Configures Content-handler.
-
last|L (last rule)
Signifies the end of the rewriting process. This option is similar to the break command in C.
-
next|N (next round)
Executes the rewriting process again from the start to the changed URL. This option is similar to the continue command in C. Warning: infinite loops are possible.
-
nocase|NC (no case)
Turns off case-sensitivity in patterns. E.g., 'A' and 'a' are considered the same.
-
noescape|NE (no URI escaping of output)
Do not use %-encoding for URL in the rewriting process.
-
nosubreq|NS (not for internal sub-requests)
Stops rewriting in the case of an internal request.
-
passthrough|PT (pass through to next handler)
Uses the result of rewriting from another handler.
-
qsappend|QSA (query string append)
When rewriting a query string, appends to the existing string instead of overwriting it.
-
redirect|R[=code] (force redirect)
When the substitute string is an absolute URL, the URL is forcibly redirected even when the hostname matches a server's host.
If the code is not specified, 302 Moved Temporarily is used. In the code, the status code can be entered directly or temp (default), permanent, and seeother can be specified.
-
skip|S=num (skip next rules)
Skip the next 'num' rules. num is a numeric value.
-
type|T=MIME-type (force MIME-Type)
Specifies the Content-Type of the response.
-
-
The following are examples of URL Rewrite.
-
Example 1
The following is an example of the URLRewriteConfig configuration that matches the URL pattern "www.test.com/" and changes it to "www.test.com/rewrite.html".
# url rewrite config - ex1 RewriteCond %{HTTP_HOST} ^www\.test\.com$ # if {Host} == "www.test.com" RewriteRule ^/$ /rewrite.html [L] # then "/" > "/rewrite.html" -
Example 2
The following is an example of a URLRewriteConfig configuration that changes a request for "www.test.com/temp/xxx.html" (and similar requests) to "www.test.com/temp/temp_error.html" when the file "xxx.html" does not exist in the temp directory.
# url rewrite config - ex2 RewriteCond %{REQUEST_FILENAME} !-f # if {Requested file name} != file or the file pointer RewriteRule ^/([^/]+) /$1/$1_error.html [L] # then "/temp/xxx.html" > "/temp/temp_error.html" -
Example 3
The following is an example of a URLRewriteConfig configuration that changes to a request for "http://www.test.com:80" (and similar requests) to "https://www.test.com:443" (http to https).
# url rewrite config - ex3 RewriteCond %{HTTP_HOST} ^www\.test\.com$ # if {Host} == "www.test.com" RewriteCond %{SERVER_PORT} 80 # AND {Port} == "80" RewriteRule .* https://www.test.com:443$0 [R] # then > "https://www.test.com:443$0" ($0: request uri) -
Example 4
The following is an example of a URLRewriteConfig configuration that matches the URL pattern "www.test.com/xxx.html" and changes it to "www.test.com/rewrite.html", ignoring Request URI.
# url rewrite config - ex4 RewriteCond %{HTTP_HOST} ^www\.test\.com$ # if {Host} == "www.test.com" RewriteRule .* http://www.test_new.com [R] # then > "http://www.test_new.com" -
Example 5
The following is an example of a URLRewriteConfig configuration that matches the URL pattern "www.test.com/test.html" and changes it to "www.test_new.com/test.html".
# url rewrite config - ex5 RewriteCond %{HTTP_HOST} ^www\.test\.com$ # if {Host} == "www.test.com" RewriteRule .* http://www.test_new.com$0 [R] # then > "http://www.test_new.com$0" ($0: request uri) -
Example 6
The following is an example of a URLRewriteConfig configuration that returns a "403 Forbidden" error when Request Method is POST and Referer Header does not exist.
# url rewrite config - ex6 RewriteCond %{REQUEST_METHOD} POST # if {Method} == "POST" RewriteCond %{HTTP_REFERER} ="" # AND {Referer} == "" RewriteRule . - [F] # then > 403 Forbidden Return -
Example 7
The following is an example of a URLRewriteConfig configuration that processes "/403.html" when a request starts with "/../".
# url rewrite config - ex7 RewriteRule ^/\.\./ /403.html [L] # Start with "/../" > "/403.html"
-
Example 8
The following is an example of a URLRewriteConfig configuration that processes "www.test.com/aaa/xxx.html" if the request is "aaa.test.com/xxx.html" and processes "www.test.com/bbb/xxx.html" if the request is "bbb.test.com/xxx.html".
# url rewrite config - ex8 RewriteCond %{HTTP_HOST} ^(aaa|bbb)\.test\.com # if {Host} == ("aaa.test.com" OR "bbb.test.com") RewriteRule .* /%1$0 [L] # then "/xxx.html" > "/(aaa|bbb)/xxx.html" (%1: Opening parenthesis of RewriteCond, $0: request uri) -
Example 9
The following is an example of a URLRewriteConfig configuration that rewrites "www.test.com/test.do?query=value1" to "www.test.com:8080/test.do?query=value1", and "www.test.com/test.do?query=value2&.." to "www.test.com:8080/test.do?query=value2&..".
# url rewrite config - ex9 RewriteCond %{QUERY_STRING} ^query=value1$ [OR] # if {QueryString} == "query=value1" RewriteCond %{QUERY_STRING} ^query=value2& # OR {QueryString} == "query=value2&.." RewriteRule .* http://www.test.com:8080$0 [R] # then > "http://www.test.com:8080$0" ($0: request uri) -
Example 10
The following is an example of a URLRewriteConfig configuration that processes "www.test.com/aaa/test.html" if the request is "aaa.test.com/test.html"(starts without 'www').
# url rewrite config - ex10 RewriteCond %{HTTP_HOST} !^www\.test\.com$ # if {Host} != www.test.com RewriteCond %{HTTP_HOST} ^([a-zA-Z0-9]+)\.test.com$ # AND {Host} == "(alphanumeric characters).test.com" RewriteRule .* /%1/$0 [L] # then > "(alphanumeric string)/$0" (%1: Opening parenthesis of RewriteCond, $0: request uri) -
Example 11
The following is an example of a URLRewriteConfig configuration that processes 403 Forbidden if the request is for css or js files when Referer Header does not exist in Request Header.
# url rewrite config - ex11 RewriteCond %{HTTP_REFERER} !. # if {HTTP_REFERER} == "" RewriteRule \.(css|js)$ - [F] # then "*.css|*.js" > 403 Forbidden Return -
Example 12(REQEUST_URI)
The following is an example of a URLRewriteConfig configuration that matches the URL pattern "/user@somehost.com/" and changes it to "/req_test.jsp?blogId=user@somehost.com".
# url rewrite config - ex12 (REQEUST_URI) RewriteCond %{REQUEST_URI} /([a-zA-Z0-9_-]+(@([a-zA-Z0-9_-]+).(com|net|co.kr))?)/?$ RewriteRule . /req_test.jsp?blogId=%1 [PT,L] -
Example 13(HTTP_HOST)
The following is an example of a URLRewriteConfig configuration that redirects requests when the HTTP Request Header's host ends with "tmaxsoft.com" and the URL starts with "/redirect/" to "http://www.tmaxsoft.com/redirect.html".
# url rewrite config - ex13 (HTTP_HOST) RewriteCond %{HTTP_HOST} tmaxsoft.com$ RewriteCond %{REQUEST_URI} /redirect/.*$ RewriteRule . http://www.tmaxsoft.com/redirect.html [R,L]
The usrinc/httpfilt.h file created during WebtoB installation provides the ISAPI (Internet Server Application Program Interface) Filter Interface. By including this file, a Filter module can be developed using the filter process provided by the WebtoB Enterprise edition.
The following is a sample filter source code that checks the client and request information.
/**
* file: sample.c for sample_filter
* Compilation example on Linux 32bit
* $ cc -m32 -D_REENTRANT -fPIC -I/webtob/usrinc -g -pthread -o sample.so sample.c -shared
*/
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include "httpfilt.h"
#define REDIRECT_PAGE "302 Moved Temporarily"
int wb_handler; /* WebtoB HTH count for only filters process */
time_t current_time;
int init()
{
int n;
/* set current time */
time(¤t_time);
n = 0;
/* n = init_check(); */
return n;
}
void url_redirect(HTTP_FILTER_CONTEXT *pfc, char *url)
{
pfc->ServerSupportFunction(pfc,
SF_REQ_SEND_RESPONSE_HEADER,
(LPVOID) REDIRECT_PAGE,
(LPDWORD) url,
0);
return;
}
/**
* called when WebtoB is booted..
**/
BOOL WINAPI
GetFilterVersion(HTTP_FILTER_VERSION * pVer)
{
DWORD dwRet;
/* Version 4.0 */
/* pVer->dwFilterVersion = MAKELONG(0, 4); */
pVer->dwFilterVersion = HTTP_FILTER_REVISION;
strncpy(pVer->lpszFilterDesc, "filter sample", SF_MAX_FILTER_DESC_LEN);
/* init when webtob is booting.. */
wb_handler = 1; /* default */
#if 0
/* only filters process is used.. */
if (0 < pVer->dwFlags) {
wb_handler = pVer->dwFlags;
pVer->dwFlags = 0;
dwRet = init();
if (dwRet < 0) {
/* init failed.. */
return 0;
}
}
#endif
/* flags */
pVer->dwFlags = (
SF_NOTIFY_SECURE_PORT |
SF_NOTIFY_NONSECURE_PORT |
SF_NOTIFY_READ_RAW_DATA |
SF_NOTIFY_PREPROC_HEADERS |
SF_NOTIFY_URL_MAP |
SF_NOTIFY_AUTHENTICATION |
SF_NOTIFY_SEND_RAW_DATA |
SF_NOTIFY_LOG |
SF_NOTIFY_END_OF_NET_SESSION |
SF_NOTIFY_ORDER_DEFAULT
);
return 1;
}
/**
* run-time callback
**/
DWORD WINAPI HttpFilterProc(HTTP_FILTER_CONTEXT *pfc, DWORD NotificationType, VOID * pvNotification)
{
DWORD dwRet;
/* init when the first request.. */
dwRet = init();
if (dwRet < 0) {
/* init failed.. */
char redirect_page[256];
sprintf(redirect_page, "Location: %s\r\n", "error.html");
url_redirect(pfc, redirect_page);
return SF_STATUS_REQ_FINISHED;
}
printf("\n\n start -> HttpFilterProc: NotificationType=%d, hth=%d \n",
NotificationType, pfc->ulReserved);
/* Direct the notification to the appropriate routine for processing. */
switch (NotificationType) {
case SF_NOTIFY_PREPROC_HEADERS:
dwRet = process_preproc_headers(pfc, (PHTTP_FILTER_PREPROC_HEADERS) pvNotification);
break;
case SF_NOTIFY_SEND_RAW_DATA:
dwRet = SF_STATUS_REQ_FINISHED_KEEP_CONN;
break;
case SF_NOTIFY_READ_RAW_DATA:
case SF_NOTIFY_URL_MAP:
case SF_NOTIFY_AUTHENTICATION:
case SF_NOTIFY_LOG:
case SF_NOTIFY_END_OF_NET_SESSION:
default:
dwRet = SF_STATUS_REQ_NEXT_NOTIFICATION;
break;
}
return dwRet;
}
/**
* process_preproc_headers
* GetHeader()
* - get the request header information
* GetServerVariable()
* - get the server variable information
* AddResponseHeaders()
* - add Response Header
* SetHeader()
* - add Request Header
* ServerSupportFunction()
* - set 302 Redirect page
**/
DWORD process_preproc_headers(HTTP_FILTER_CONTEXT *pfc, HTTP_FILTER_PREPROC_HEADERS *pvNotification)
{
/* watch out buffer size */
int size;
char request_method[32];
char request_uri[8192];
char client_ip[256];
char server_port[32];
char content_type[256];
char content_length[256];
char body[10240];
char s_header[8192];
char cookie[8192];
char add_res_header[8192];
char redirect_page[8192];
int redirect_test = 0;
int setcookie_test = 1;
/* ssl y/n */
printf("Request is SSL? %d \n", pfc->fIsSecurePort);
/* get request method */
size = sizeof(request_method);
memset(request_method, 0, size);
/* pvNotification->GetHeader(pfc, "method", request_method, &size); */
pfc->GetServerVariable(pfc, "REQUEST_METHOD", request_method, &size);
printf("Request Method? %s \n", request_method);
/* get request url */
size = sizeof(request_uri);
memset(request_uri, 0, size);
/* pvNotification->GetHeader(pfc, "url", request_uri, &size); */
pfc->GetServerVariable(pfc, "REQUEST_URI", request_uri, &size);
printf("Request url? %s \n", request_uri);
/* get client ip */
size = (int) sizeof(client_ip);
memset(client_ip, 0, size);
pfc->GetServerVariable(pfc, "REMOTE_ADDR", client_ip, &size);
printf("Client ip? %s \n", client_ip);
/* get server port */
size = (int) sizeof(server_port);
memset(server_port, 0, size);
pfc->GetServerVariable(pfc, "SERVER_PORT", server_port, &size);
printf("Server Port? %s \n", server_port);
/* get Content-Type Request Header */
size = (int) sizeof(content_type);
memset(content_type, 0, size);
pvNotification->GetHeader(pfc, "Content-Type", content_type, &size);
printf("Content-Type? %s \n", content_type);
/* get Content-Length Request Header */
size = (int) sizeof(content_length);
memset(content_length, 0, size);
pvNotification->GetHeader(pfc, "Content-Length", content_length, &size);
printf("Content-Length? %s \n", content_length);
/* get Cookie Request Header */
size = (int) sizeof(cookie);
memset(cookie, 0, size);
pvNotification->GetHeader(pfc, "Cookie", cookie, &size);
printf("Cookie? %s \n", cookie);
/* get special header */
size = sizeof(s_header);
memset(s_header, 0, size);
pvNotification->GetHeader(pfc, "Special-Header", s_header, &size);
printf("Special-Header? %s \n", s_header);
/* get body data */
if (content_length) {
size = (int) sizeof(body);
memset(body, 0, size);
pvNotification->GetHeader(pfc, "body", body, &size);
printf("Body? %s \n", body);
}
/* add Response Header on processing request */
if (setcookie_test) {
sprintf(add_res_header, "Set-Cookie: %s=%s; path=/; domain=test\r\n", "TestKey", "TestValue");
pfc->AddResponseHeaders(pfc, add_res_header, 0);
}
sprintf(add_res_header, "AddResponseHeader: test");
pfc->AddResponseHeaders(pfc, add_res_header, 0);
/* add Request Header */
pvNotification->SetHeader(pfc, "addReuestHeader", "test value");
/* 302 redirect */
if (redirect_test) {
sprintf(redirect_page, "Location: %s\r\n", "test/redirect.html");
url_redirect(pfc, redirect_page);
return SF_STATUS_REQ_FINISHED;
}
return SF_STATUS_REQ_NEXT_NOTIFICATION;
}