Table of Contents
This chapter gives an overview of Tmax application programs and describes their structure and characteristics.
Tmax application programs are client/server programs developed in an open environment that uses Tmax as middleware. The emergence of high-performance PCs and the development of programming technologies have brought about changes from central computing to client/server environments, where task processing is divided between clients and servers. Client/server computing has enabled efficient utilization of resources including the use of high-performance PCs, the scaling down of servers, and the expansion of hardware options.
The client/server environment, however, still has the following problems:
-
Developers must have in-depth knowledge of hardware, operating systems, and network protocols.
-
An increase in the number of users or the amount of data immediately leads to a sharp decrease in computing speed.
-
Excessive network traffic decreases computing speed.
-
A distributed environment creates problems related to process management, communication, security, and error handling.
Tmax application programs remedy the drawbacks of client/server programs while maintaining their benefits. Application programs based on Tmax as middleware are used to manage communication programs, processes, and transactions. Tmax functions are divided into server library (libsvr.a) and client library (libcli.a) functions that handle buffers, communication, and transactions. These functions comply with the X/Open Data Transaction Processing (DTP) model, which is the international standard for distributed processing.
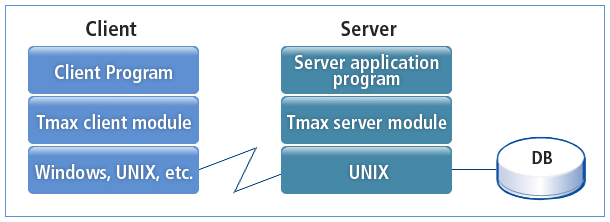
A Tmax application program consists of a client program and a server program. It requires an environment configuration to use Tmax.
-
Client programs request services on behalf of users, receive results from a server, and return the results to users in the user-specified format. These programs require the UNIX configuration file (e.g., the .profile file). The UNIX configuration file is used to configure the information, such as the address and port number, necessary for clients to connect to Tmax. Client programs refer to relevant binary files when connecting to Tmax and use structure buffers or field buffers with environment variables in the user configuration file.
-
Server programs receive requests from clients, control access to system resources, process client requests, and return the results to clients.
Server programs consist of the main() task, which is provided and managed by Tmax, and service routines developed by developers. Service routines and service tables created with Tmax utilities are compiled together. If a structure buffer is used, a conversion routine created with a Tmax utility must be run.
Tmax application servers need server programs and the Tmax configuration file. The Tmax configuration file defines the entire system environment of resources and is written by the administrator. The configuration file is referenced when the Tmax server and server programs are launched. The configuration file is also referenced when service tables are created.
The following figure shows the structure of a Tmax application program:
Note
For more information on client/server programs, refer to "Chapter 2. Client Program" and "Chapter 3. Server Program".
The following are the differences between UNIX programs and Tmax application programs.
-
Programs comply with the X/Open DTP model, the international standard for distributed processing.
Routines that control the network use Tmax functions, which comply with the X/Open DTP model. Programs developed in other middleware that comply with the X/Open DTP model are compatible with Tmax.
-
Programs only required service routines that handle client requests.
Client must develop programs using general C language syntax, which includes main(). Server programs only require request processing routines, which do not include main().
-
Service requests can be issued in one of three communication modes.
Synchronous, asynchronous, and interactive communication modes are supported. With these modes, developers can easily develop programs without deep knowledge of communication networks.
The following are descriptions of each mode.
Communication Mode Description Synchronous Communication Waits for a response after requesting a service request (tpcall). Asynchronous Communication After requesting a service (tpacall), other tasks are executed until a response (tpgetrply) is received. Interactive Communication Sends (tpsend) and receives (tprecv) messages repeatedly after the initial connection is made (tpconnect). Note
For more information about communication modes, refer to "Chapter 4. Communication Mode".
-
Seven types of buffers can be used.
7 types of buffers can be used to request a service. Data integrity is difficult to guarantee for data communication between heterogeneous systems. Different hardware and OSs use different methods to allocate memory for data or define data length by data type. I.e., a receiver may recognize received data as a value different than the value the sender intended. Therefore, before being transmitted or received, data is converted into a string that all hardware and OSs involved can recognize.
Because Tmax supports various buffers, developers can easily develop programs without deep knowledge of machines, operating systems, and networks. Tmax enhances system performance and reduces network load by providing various buffers including the structure type and the string type.
Note
For more information on buffers, refer to "Chapter 5. Buffer Type".
-
Program development is simple.
-
Developers can develop programs without deep knowledge of hardware and communication networks.
-
Clients can request services without knowing the address of the server that handles the request.
-
Clients can request services only with a name.
-
-
Transaction integrity is guaranteed.
If the range of transactions is set in a program, Tmax guarantees transaction integrity with 2PC.
Note
2PC (two-phase commit) handles transactions in 2 phases (prepare phase and commit phase) when two or more databases are integrated. For more information, refer to "Chapter 6. Transaction".