Table of Contents
This chapter briefly explains some approaches to security, including encrypting the password that is required to use JEUS server and manage accounts. The security information is shared by all servers in the domain and is configured using DAS.
Note
Refer to "JEUS Security Guide" for detailed information about JEUS security.
JEUS has both user and group accounts.
In JEUS, roles are granted rights to the resources. These rights are granted to the user by assigning the user to the role.
There are three ways to assign a role to a user.
-
Assign the role to a user name
-
Assign the role to a group that the user belongs to
-
Assign the role to a parent group of the group that the user belongs to
Since the account hierarchy consists of users, groups, and subgroups, users with similar roles in JEUS can be granted similar permissions at once.
Refer to JEUS Security Guide. "2.6. Configuring Security System Policies" for detailed information about security policies.
Passwords for system management can be encrypted and stored.
The encrypted information is stored in the following format.
{Algorithm}Cryptogram
The following encryption algorithms are available for use.
-
AES
-
DES
-
DESede
-
blowfish
-
SEED
The password can be encrypted and stored using WebAdmin or the console tool, or manually by using the encryption tool. This section describes each method.
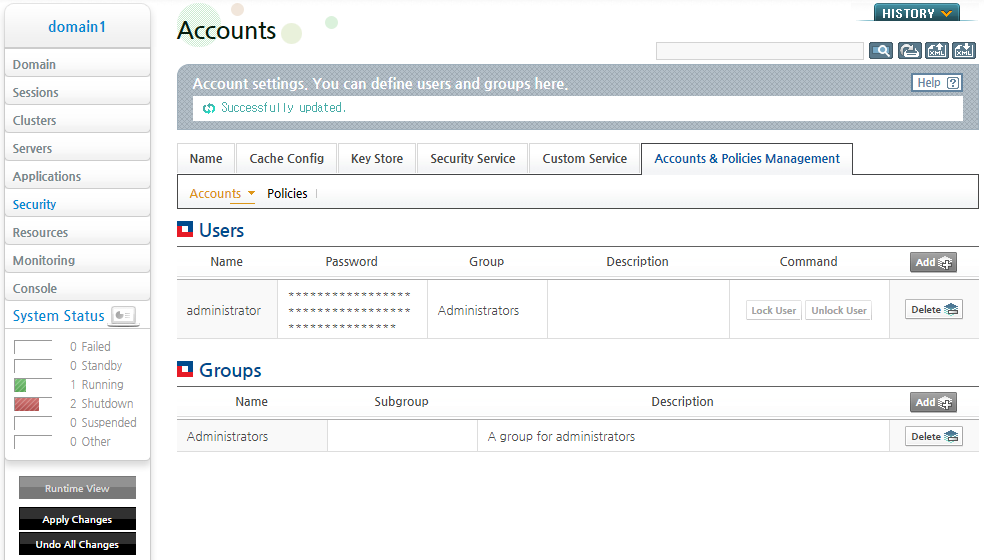
The following is an example of configuring the user account password using WebAdmin.
-
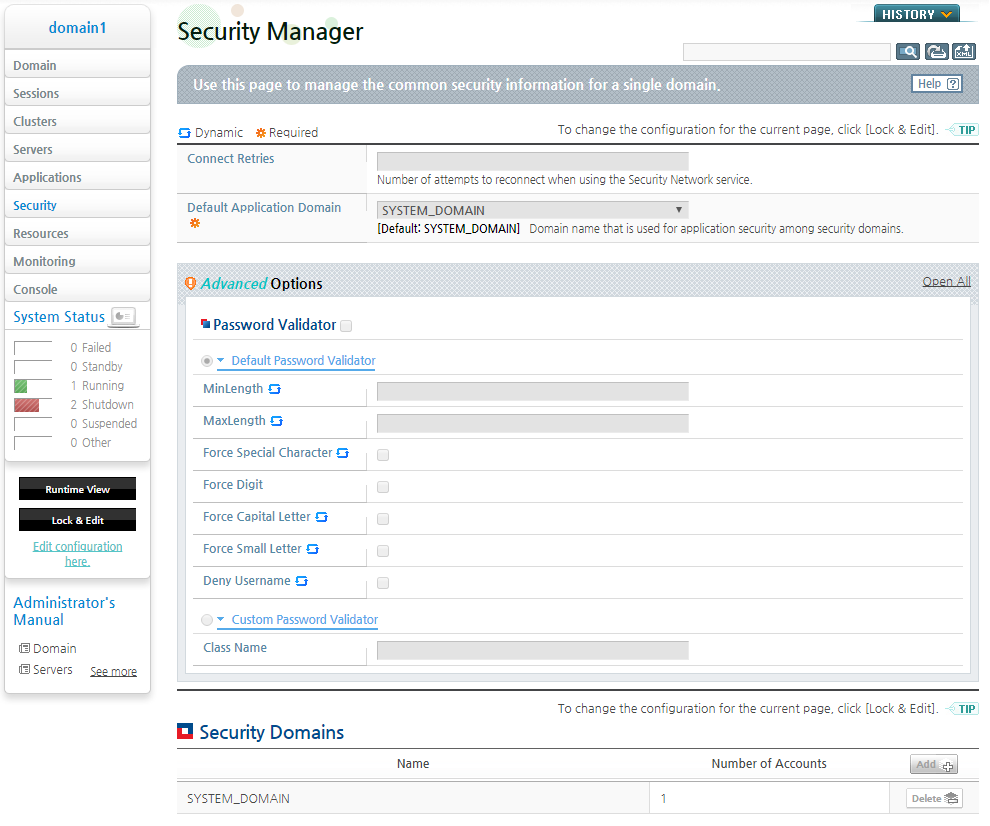
Click [Security] from the left menu. Click the security domain from the list of Security Domains on the Security Manager screen.
-
Click [Lock & Edit] to change to the configuration mode.
Refer to JEUS WebAdmin Guide. "2.3.2. Menu" for detailed information about the configuration mode in WebAdmin.
-
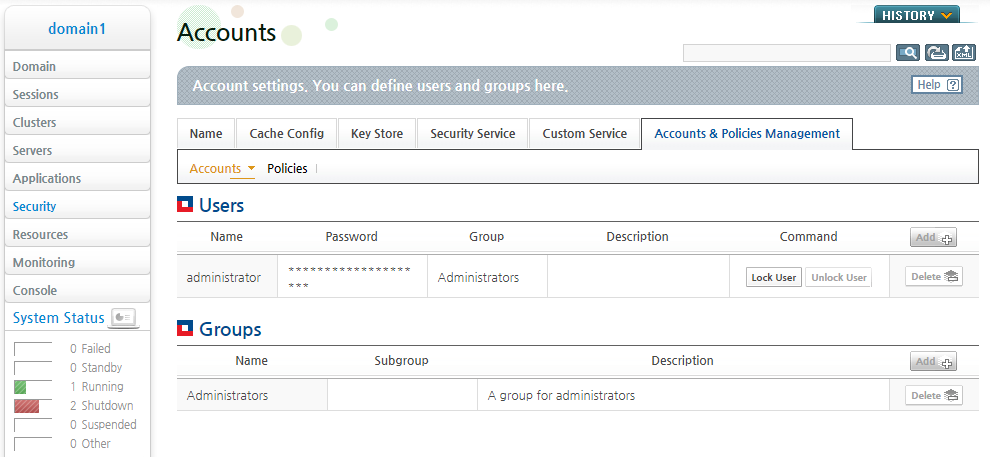
Go to [Accounts & Policies Management] > [Accounts], and select a user name for which to change the password from the Users table.
-
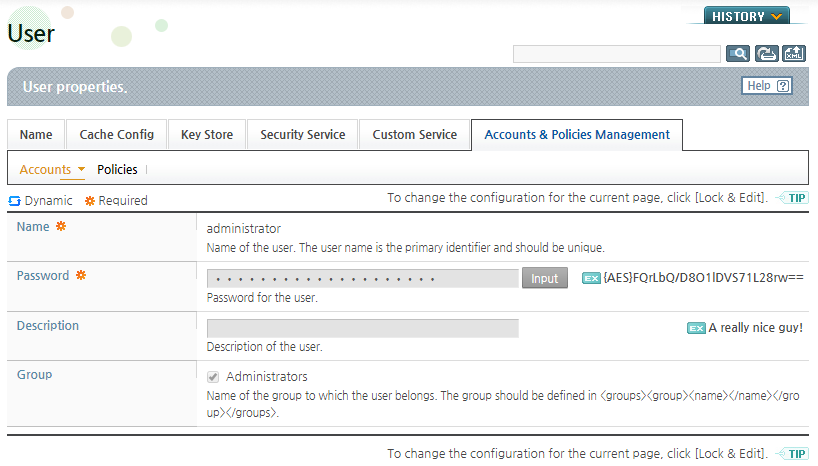
Click [Input] next to the 'Password' field on the User screen.
-
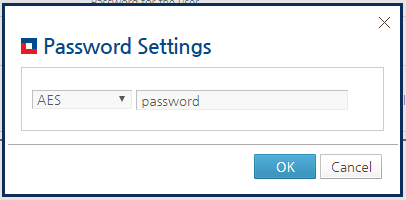
Select the algorithm to use for password encryption, enter the password, and click [OK].
-
After entering the password, click [OK] and then click [Apply Changes] to immediately apply the changes.
-
If the password for the current user is changed, the user must log out and log back in. If the password of another user is changed, the result message is displayed.
The following is an example of encrypting and storing the password "password' for the account "administrator" using the AES encryption algorithm through the console tool jeusadmin.
[DAS]domain1.adminServer>set-password administrator password -algorithm AES
The password is set for [administrator].
[DAS]domain1.adminServer>exit
JEUS_HOME/bin$ jeusadmin -u administrator -p password
Attempting to connect to 127.0.0.1:9736.
The connection has been established to Domain Administration Server adminServer
in the domain domain1.
JEUS8 Administration Tool
To view help, use the 'help' command.
The password can be manually encrypted using an encryption tool. For example, the DB password and the passwords in accounts.xml can be encrypted instead of using plain text.
The encrypted text is configured in the following format anywhere a password is required.
{Algorithm}Cryptogram
Use the encryption tool provided by JEUS to encrypt the string. Enter the string to encrypt and the algorithm, and the tools will output the encrypted text.
Note
Refer to JEUS Reference Book. "4.6. encryption" for detailed information about the encryption tools.
Both base64 are hashing algorithms that always produce the same output for a given string. Other algorithms require a secret key. Refer to "7.3. Managing the Secret Key File" for detailed information about how to manage this secret key.
The following is an example of configuring an encrypted password in accounts.xml.
[Example 7.1] Using Encryption Tool - <<accounts.xml>>
<accounts xmlns="http://www.tmaxsoft.com/xml/ns/jeus">
<users>
<user>
<name>administrator</name>
<password>{base64}amV1czEyMw==</password>
</user>
<user>
<name>user1</name>
<password>{AES}i06wYRz3Gqun2sKtXHIq+Tw3vUcc=</password>
</user>
. . .
</users>
. . .
</accounts>
Note
XML can be directly edited when a domain is first created, but afterward it is recommended to use WebAdmin or the console tool, jeusadmin.
This section describes how to create, manage, and protect the secret key file.
The AES, DES, DESede, SEED, and BlowFish algorithms that are provided by the encryption tool in 'JEUS_HOME/bin' require a secret key to encrypt or decrypt. JEUS stores the secret key in a file. This file is automatically created when the encryption tool is used for the first time.
The file is named security.key and can be found in the following path.
JEUS_HOME/domains/<domain-name>/config/security
The path can be configured with the system property jeus.security.keypath which can be an absolute or relative path. For a relative path, the base path is the path to JVM. If the path points to a directory, the security.key file in that directory is used. If the path points to a file, that file is used.
JEUS can encrypt the secret key file. A password called the master password is required to encrypt the secret key file. Use the -protectkey option with the encryption tool to protect the secret key file with this master password.
The master password is required to start a server.
There are two ways to enter the master password.
-
If a server is started by a background process, the master password can be set in the jeus.security.master system property.
-
If a server is started by JEUS script, the master password can be entered in the console tool.
Using a shell script to set the master password in jeus.security.master is not secure. It is recommended to directly enter the master password in the console tool.
Note
1. Refer to JEUS Reference Book. "Chapter 3. Starting JEUS Server" for detailed information about starting a server.
2. Refer to JEUS Reference Book. "4.6. encryption" for detailed information about secret keys.
This section briefly describes how to manage the keystore and truststore that are used in SSL communication.
Both keystore and truststore are a Java Key Store (JKS). They can be created and managed by using key tools provided by the JDK.
Note
For detailed information about JSSE, JKS, and keytools, refer to the Java documentation. For detailed information about keystores, truststores, and SSL, refer to http://www.oracle.com/technetwork/java/index.html .
By default, JEUS uses the following files as the keystore and truststore. To use an alternate path or file name, it must be configured manually.
The properties can be configured at the system level or separately wherever a keystore and truststore are needed.
The following describes each system property.
A password is required to use a keystore or truststore. As previously mentioned, the passwords for the keystore and truststore can be configured in JEUS. Similar to the file path setting, passwords can be configured at the system level or separately as needed.
A keystore requires a password for the keys in the keystore, and a password for the keystore itself. In general, the key password is same as the keystore password.
If the key password is different from the repository's password, set the key password in <keystore-keypassword>. Also, in order to use the keystore all the keys in the keystore must use the same key password.
Note
Although a keystore and truststore are created when JEUS is installed, it is recommended to create and configure them manually.
This section describes the configurations that must be added to various executable scripts when the Base Listener of each server is set to SSL in the domain.
When setting each server in the domain to SSL, the server's SSL configuration is used for inter-server communication. However, additional SSL configuration is required for the processes that run on the client side such as Console Admin or executable scripts.
Additional configurations are required for the following.
In the following example, the bolded texts are the configurations that must be added to the scripts.
[Example 7.2] jeusadmin script that specifies SSL-related client configurations
. . .
# execute jeusadmin
"${JAVA_HOME}/bin/java" -classpath "${BOOTSTRAP_CLASSPATH}" ${TOOL_OPTION}
-Djmx.remote.x.request.timeout=600000
-Djava.library.path="${JEUS_LIBPATH}"
-Djeus.home="${JEUS_HOME}"
-Djeus.baseport=${JEUS_BASEPORT}
-Djeus.tool.console.useJLine="false"
-Djava.endorsed.dirs="${JEUS_HOME}/lib/endorsed"
-Djava.naming.factory.initial=jeus.jndi.JEUSContextFactory
-Djava.naming.factory.url.pkgs=jeus.jndi.jns.url
-Djava.util.logging.config.file="${JEUS_HOME}/bin/logging.properties"
-Djeus.net.client.use-ssl=true
-Djavax.net.ssl.trustStore=${JEUS_HOME}/domains/domain1/config/truststore
-Djavax.net.ssl.trustStorePassword=changeit
-Djavax.net.ssl.trustStoreType=JKS
-Dssl.TrustManagerFactory.algorithm=SunX509
-Djavax.net.ssl.keyStore=${JEUS_HOME}/domains/domain1/config/keystore
-Djavax.net.ssl.keyStorePassword=changeit
-Djavax.net.ssl.keyStoreType=JKS
-Dssl.KeyManagerFactory.algorithm=SunX509
-Djeus.security.keypath=${JEUS_HOME}/domains/domain1/config/security/security.key
${JAVA_ARGS}
jeus.tool.console.ConsoleBootstrapper ${BOOT_PARAMETER}
The bolded text is a separate file that contains the SSL-related client configurations.
[Example 7.3] jeusadmin script that specifies a separate file containing SSL-releated client configurations
. . .
# execute jeusadmin
"${JAVA_HOME}/bin/java" -classpath "${BOOTSTRAP_CLASSPATH}" ${TOOL_OPTION}
-Djmx.remote.x.request.timeout=600000
-Djava.library.path="${JEUS_LIBPATH}"
-Djeus.home="${JEUS_HOME}"
-Djeus.baseport=${JEUS_BASEPORT}
-Djeus.tool.console.useJLine="false"
-Djava.endorsed.dirs="${JEUS_HOME}/lib/endorsed"
-Djava.naming.factory.initial=jeus.jndi.JEUSContextFactory
-Djava.naming.factory.url.pkgs=jeus.jndi.jns.url
-Djava.util.logging.config.file="${JEUS_HOME}/bin/logging.properties"
-Djeus.net.client.ssl-properties-file=ssl.properties
${JAVA_ARGS}
jeus.tool.console.ConsoleBootstrapper ${BOOT_PARAMETER}
The following is an example file that defines SSL-releated client configurations. Note that a relative path beginning with ${JEUS_HOME} cannot be used in a file.
[Example 7.4] SSL-related client configuration - <<ssl.properties>>
javax.net.ssl.keyStore=/Users/ccs/workspace/JEUS8/target/jeus/domains/domain1/config/keystore
javax.net.ssl.trustStore=/Users/ccs/workspace/JEUS8/target/jeus/domains/domain1/config/truststore
javax.net.ssl.keyStorePassword=jeus
javax.net.ssl.trustStorePassword={AES}i06wYRz3Gqun2sKtXHIq+Tw3vUcc=
jeus.ssl.keystorekeypass={base64}amV1czEyMw==
jeus.security.keypath=/Users/ccs/workspace/JEUS8/target/jeus/domains/domain1/config/security/security.key
The password property can be set to an encoded or encrypted character string in the same way that they are used in accounts.xml. Use the encryption tool provided by JEUS.
Note
1. For more information about the encryption tool, refer to JEUS Reference Book. "4.6. encryption".
2. To use domains in an SSL environment, the SSL must be also specified in the Node Manager, Refer to JEUS Node Manager Guide. "2.3.1. Configuration File" for detailed information.